I just did a fresh Virtualbox VM with 22.0.5 as base and updated to today’s stable update of 2023-04-11. The install used the automatic install mode with LUKS encryption using a normal password.
Boot process:
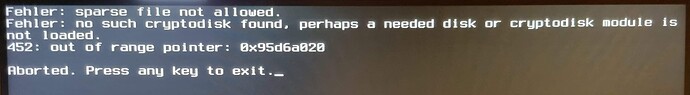
Now I’ve to see what changed and how to get that message away.
how I got rid of the nag screen
- I had to reinstall grub via
grub-install --force --target=i386-pc --recheck --boot-directory=/boot /dev/sda
- then I ran
update-grub to regenerate the menu
This got rid of the nag screen not finding the right partition.
Lets analyze the grub.cfg file of the old grub installed to MBR on this BIOS VM:
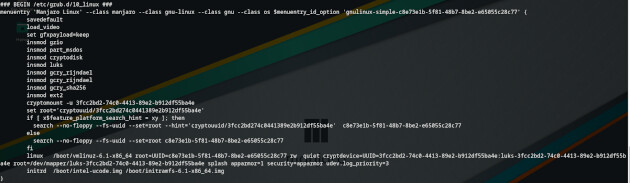
So it loads the needed modules. calls cryptomount -u and points to the right partitions.
After I also updated grub on MBR we got this menu entry for the same 6.1 kernel:
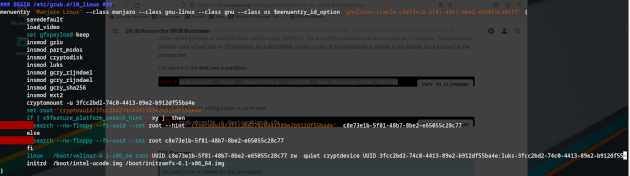
More or less it is the same entry as we had before. So the only change most likely made is on the binary files which got installed by the package update of grub package. Most similar on that issue, on which we reverted those modifications to call fwsetup: Arch Linux - News: Grub bootloader upgrade and configuration incompatibilities
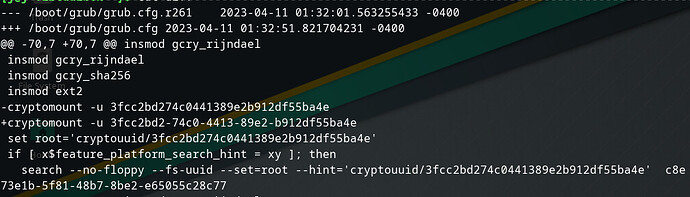
Me and the dashes …
Seems grub 2.06-r261 has the cryptomount -u cmd without the dashes and with 2.06-r456 those got added. So removing the dashes from the cmd “fixes” the issue. However, those changes are common and only get fixed when grub matches the binaries of the package and the version installed on MBR/EFI.
So what is the real issue now?
-
commit 3cf2e84 changes how UUIDs for cryptodisk got handled.
- a user can now specify UUID strings with dashes, instead of having to remove
dashes. This is backwards-compatibility preserving and also fixes a source
of user confusion over the inconsistency with how UUIDs are specified
between file system UUIDs and cryptomount UUIDs. Since cryptsetup, the
reference implementation for LUKS, displays and generates UUIDs with dashes
there has been additional confusion when using the UUID strings from
cryptsetup as exact input into GRUB does not find the expected cryptodisk.
- since we never update the corresponding MBR/EFI installation of grub, which needs to been called via
grub-install and the parameters used to install grub the first time those changes in the binary files of the grub package won’t match the expectations the older grub may have from grub.cfg file. Hence it is a breaking change for older installations
- Is Arch affected by this? Most likely yes when they updated their package to 2:2.06.r380.g151467888-1. But there people expect to know on how to fix issues with grub, especially when you use LUKS FDE.
What is the real fix?
Well Arch needs to fix on how it installs grub to begin with as upstream expects to have their binaries in sync with what the package installs on your hard drive and what is installed in your MBR/EFI.
Is there a workaround?
Sure, you can modify /usr/bin/update-grub by removing execand add the following line: sed -i -e '/cryptomount -u/ {s/-//g;s/ u/ -u/g}' /boot/grub/grub.cfg after the line which starts now with grub-mkconfig ...
How can I avoid all of that matter?
Simply put grub into the package ignore list as grub won’t get properly installed anyway.
What about security updates?
Well, you’re the admin of your machine. Update grub package and keep your MBR/EFI installation of grub in-sync