Hello,
I did a clean installation of manjaro (KDE) few days ago on my laptop.
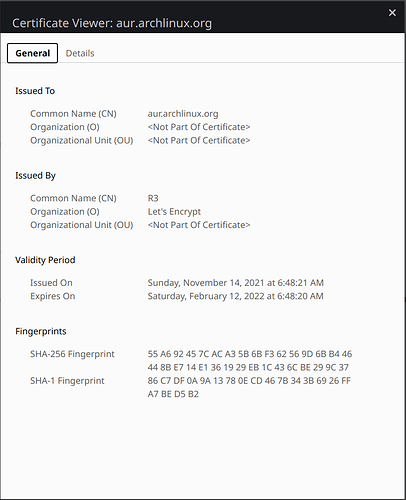
Since then, I was unable to install anything from AUR, because my laptop thinks that the AUR SSL certificate is expired, while it’s completely valid and working fine for others.
I was able to reduce it to simple reproducer, a single curl command
my laptop:
curl -vI https://aur.archlinux.org ✔
* Trying 95.216.144.15:443...
* Connected to aur.archlinux.org (95.216.144.15) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: none
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (OUT), TLS alert, certificate expired (557):
* SSL certificate problem: certificate has expired
* Closing connection 0
curl: (60) SSL certificate problem: certificate has expired
More details here: https://curl.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
any other computer:
» curl -vI https://aur.archlinux.org
* Trying 95.216.144.15:443...
* Connected to aur.archlinux.org (95.216.144.15) port 443 (#0)
* ALPN, offering h2
* ALPN, offering http/1.1
* successfully set certificate verify locations:
* CAfile: /etc/ssl/cert.pem
* CApath: none
* TLSv1.2 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS handshake, Server key exchange (12):
* TLSv1.2 (IN), TLS handshake, Server finished (14):
* TLSv1.2 (OUT), TLS handshake, Client key exchange (16):
* TLSv1.2 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS handshake, Finished (20):
* TLSv1.2 (IN), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (IN), TLS handshake, Finished (20):
* SSL connection using TLSv1.2 / ECDHE-RSA-AES256-GCM-SHA384
* ALPN, server accepted to use h2
* Server certificate:
* subject: CN=aur.archlinux.org
* start date: Nov 14 05:48:21 2021 GMT
* expire date: Feb 12 05:48:20 2022 GMT
* subjectAltName: host "aur.archlinux.org" matched cert's "aur.archlinux.org"
* issuer: C=US; O=Let's Encrypt; CN=R3
* SSL certificate verify ok.
* Using HTTP2, server supports multi-use
* Connection state changed (HTTP/2 confirmed)
* Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0
* Using Stream ID: 1 (easy handle 0x7f7a7780d600)
> HEAD / HTTP/2
> Host: aur.archlinux.org
> user-agent: curl/7.77.0
> accept: */*
>
* Connection state changed (MAX_CONCURRENT_STREAMS == 128)!
< HTTP/2 200
HTTP/2 200
< server: nginx
server: nginx
< date: Tue, 04 Jan 2022 13:55:14 GMT
date: Tue, 04 Jan 2022 13:55:14 GMT
< content-type: text/html; charset=utf-8
content-type: text/html; charset=utf-8
< cache-control: no-cache, must-revalidate
cache-control: no-cache, must-revalidate
< expires: Tue, 11 Oct 1988 22:00:00 GMT
expires: Tue, 11 Oct 1988 22:00:00 GMT
< pragma: no-cache
pragma: no-cache
< x-frame-options: DENY
x-frame-options: DENY
< strict-transport-security: max-age=31536000; includeSubdomains; preload
strict-transport-security: max-age=31536000; includeSubdomains; preload
<
* Connection #0 to host aur.archlinux.org left intact
echo | openssl s_client -showcerts -servername aur.archlinux.org -connect aur.archlinux.org:443 2>/dev/null | openssl x509 -inform pem -noout -text | grep -A 2 Validity
Validity
Not Before: Nov 14 05:48:21 2021 GMT
Not After : Feb 12 05:48:20 2022 GMT
I found what seems related, but don’t know how to verify/check/fix this, but it’s a year old issue
I obviously tried to install different AUR helpers until I realized it’s not AUR/helpers, but my system which for some reason thinks that the certs are invalid.
Any ideas how to fix it? I don’t even know where to start looking.
Thank you.