see this.
Using the AUR on Manjaro stable branch is officially supported this much - ![]()
yt-dlp version 2024.03.10-1 is available on Unstable and Testing branches
packages.manjaro.org - yt-dlp
I tried to install Persepolis package 3.2.0-8 from main repo but noticed its dependecy youtube-dl which is on AUR only and no longer maintained. I’m on stable branch.
Checking Packages shows that unstable/testing branch got updated persepolis package 4.0.1 which must have happend sometime in early/mid march. Commits · main · Arch Linux / Packaging / Packages / persepolis · GitLab.
Persepolis 4.0.x changed dependency to yt-dlp which is on the main repo.
Is there a way to also get persepolis 4.0.1 on stable?
The easiest is to wait until 4.0.1 filters down to the lower levels. I imagine it won’t be too far away.
Failing that, I notice Persepolis-git 4.0.1 is available with a yt-dlp dependency, if that will suffice in the meantime:
A post was split to a new topic: Glibc is a bit flaky when using chrootbuild
Vulnerability of Flatpak, please provide a newer version than 1.15.6 in Stable
The sandbox system is said to be able to run arbitrary code if the application includes such.
You can perform a simple test to verify whether your system is affected. [Run] any Flatpak application and run it with the
--command=--helpfollowed by the application’s ID. If the system returns an error message stating that the help command is not found, your Flatpak installation is not vulnerable.
However, if it displays an output similar to that of the
bwrap --helpcommand, it means your version is still at risk.
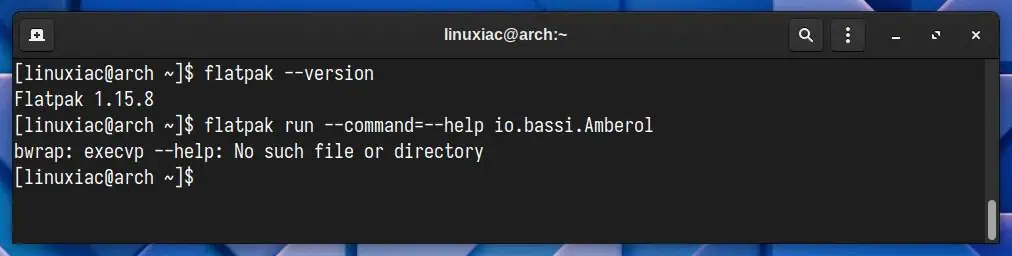
So I did test it and selected one.ablaze.floorp from my apps listed in flatpak list
I have version
flatpak --version
Flatpak 1.15.6
And I concluded Stable is affected because this is the output of (replace “one.ablaze.floorp” with any long name of your installed apps listed under flatpak list)
flatpak run --command=--help one.ablaze.floorp ✔ at 14:02:17
usage: bwrap [OPTIONS...] [--] COMMAND [ARGS...]
--help Print this help
--version Print version
--args FD Parse NUL-separated args from FD
--unshare-all Unshare every namespace we support by default
--share-net Retain the network namespace (can only combine with --unshare-all)
--unshare-user Create new user namespace (may be automatically implied if not setuid)
--unshare-user-try Create new user namespace if possible else continue by skipping it
--unshare-ipc Create new ipc namespace
--unshare-pid Create new pid namespace
--unshare-net Create new network namespace
--unshare-uts Create new uts namespace
--unshare-cgroup Create new cgroup namespace
--unshare-cgroup-try Create new cgroup namespace if possible else continue by skipping it
--userns FD Use this user namespace (cannot combine with --unshare-user)
--userns2 FD After setup switch to this user namespace, only useful with --userns
--disable-userns Disable further use of user namespaces inside sandbox
--assert-userns-disabled Fail unless further use of user namespace inside sandbox is disabled
--pidns FD Use this pid namespace (as parent namespace if using --unshare-pid)
--uid UID Custom uid in the sandbox (requires --unshare-user or --userns)
--gid GID Custom gid in the sandbox (requires --unshare-user or --userns)
--hostname NAME Custom hostname in the sandbox (requires --unshare-uts)
--chdir DIR Change directory to DIR
--clearenv Unset all environment variables
--setenv VAR VALUE Set an environment variable
--unsetenv VAR Unset an environment variable
--lock-file DEST Take a lock on DEST while sandbox is running
--sync-fd FD Keep this fd open while sandbox is running
--bind SRC DEST Bind mount the host path SRC on DEST
--bind-try SRC DEST Equal to --bind but ignores non-existent SRC
--dev-bind SRC DEST Bind mount the host path SRC on DEST, allowing device access
--dev-bind-try SRC DEST Equal to --dev-bind but ignores non-existent SRC
--ro-bind SRC DEST Bind mount the host path SRC readonly on DEST
--ro-bind-try SRC DEST Equal to --ro-bind but ignores non-existent SRC
--remount-ro DEST Remount DEST as readonly; does not recursively remount
--exec-label LABEL Exec label for the sandbox
--file-label LABEL File label for temporary sandbox content
--proc DEST Mount new procfs on DEST
--dev DEST Mount new dev on DEST
--tmpfs DEST Mount new tmpfs on DEST
--mqueue DEST Mount new mqueue on DEST
--dir DEST Create dir at DEST
--file FD DEST Copy from FD to destination DEST
--bind-data FD DEST Copy from FD to file which is bind-mounted on DEST
--ro-bind-data FD DEST Copy from FD to file which is readonly bind-mounted on DEST
--symlink SRC DEST Create symlink at DEST with target SRC
--seccomp FD Load and use seccomp rules from FD (not repeatable)
--add-seccomp-fd FD Load and use seccomp rules from FD (repeatable)
--block-fd FD Block on FD until some data to read is available
--userns-block-fd FD Block on FD until the user namespace is ready
--info-fd FD Write information about the running container to FD
--json-status-fd FD Write container status to FD as multiple JSON documents
--new-session Create a new terminal session
--die-with-parent Kills with SIGKILL child process (COMMAND) when bwrap or bwrap's parent dies.
--as-pid-1 Do not install a reaper process with PID=1
--cap-add CAP Add cap CAP when running as privileged user
--cap-drop CAP Drop cap CAP when running as privileged user
--perms OCTAL Set permissions of next argument (--bind-data, --file, etc.)
--size BYTES Set size of next argument (only for --tmpfs)
--chmod OCTAL PATH Change permissions of PATH (must already exist)
So if possible, please provide a newer version in Stable.
From the above link:
Thankfully, the Flatpak team has promptly responded with patches to this vulnerability. Users are strongly encouraged to update their Flatpak installations to the following versions to ensure they are protected:
** [I think does not count for Manjaro Stable!]> [ For users on the stable branch, Flatpak version 1.14.6 or newer.]**
** For those on older stable branches, version 1.12.9 or 1.10.9 are the safe bets.**
** Developers using the developmental branch should update to version 1.15.8 or above.**
I think Manjaro based on Arch goes by the third option what they call developmental branch!
All the above - quoted/pics is from Flatpak Patch Addresses Major Sandbox Escape Flaw
I guess we will get the fix pretty quickly. The updated version is already in testing branch, and since stable was not updated for over a month i think it will soon be time for an update, resp. that the testing versions hit stable.
Thank you for looking it up. I didn’t know I could update to the 1.15.8 version with manjaro-downgrade command. But maybe do not follow what I just did ![]() Will not run any flatpak now
Will not run any flatpak now ![]()
Sorry, not possible to fast-track it at this time. The flatpak package has quite a view other dependencies.
![]() We have a testing and unstable branches for a reason. If users want to help the stable branch actually live up to it’s namesake, the more users using the aforementioned other two branches will help with that. Keep in mind the Manjaro unstable branch is on par with Arch stable. Don’t let the branch name fool you.
We have a testing and unstable branches for a reason. If users want to help the stable branch actually live up to it’s namesake, the more users using the aforementioned other two branches will help with that. Keep in mind the Manjaro unstable branch is on par with Arch stable. Don’t let the branch name fool you. ![]()
Hello
The current version 0.9.35 of Manjaro contains a bug that prevents the import of videos. The developer has fixed the bug in version 0.9.36. Is it enough to make this known here, or is there a better way?
edit:
ok i understand. i mark it as out of date in the arch repos. is that correct?
Current version of what?
rapid-photo-downloader - here’s the original request thread:
Arch Linux - rapid-photo-downloader 0.9.35-2
Flagged out-of-date on 2024-02-20
gpodder is using a module that is deprecated in python 3.12 and does not start at all. According to the issue in github there is already a patch and a new package in arch. Please fasttrack to all branches.
Any reason not to upgrade ffmpeg from version 6 to 7???
Additionnaly, opus codec has had major improvements
https://ffmpeg.org/index.html#news
Thanks
You have to ask arch about that, this is an arch package.
Arch Linux - ffmpeg 2:6.1.1-7 (x86_64)
Flagged out-of-date on 2024-04-05
Arch Linux - opus 1.5.2-1 (x86_64)
packages.manjaro.org - opus
A post was merged into an existing topic: Update requests for packages built by Manjaro developers
After last stable update, amule 2.3.3-8 stop working as seen here:
I have installed amule 2.3.3-9 from unstable repository and works fine. As is only one package, maybe it could be updated already.