I have just switched from Debian to Manjaro. On Debian I was running KDE Plasma (Wayland) together with GDM3. There I had disabled the Gnome keyring and replaced it with KeePassXC. Everything worked fine so far, all apps automatically used KeePassXC instead of kwallet.
Now I wanted to have this under Manjaro as well. And the setup is similar, except that I use SDDM as installed by default. Otherwise also KDE Plasma (Wayland). I figured that since there is no GDM3, there is no Gnome keyring that needs to be disabled.
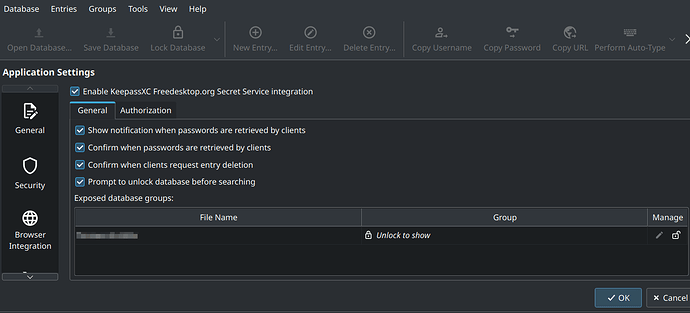
KeePassXC set up and it works so far. When I save or retrieve passwords with the command line tool secret-tool, this all ends up in KeeyPassXC.
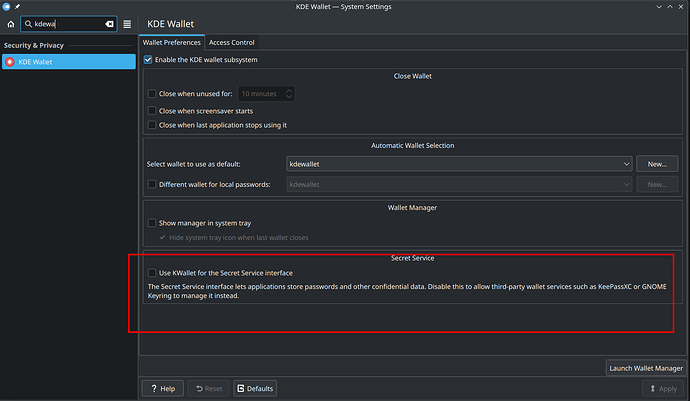
But the many other KDE applications generally refuse to go via libsecret, but persistently want to access kwallet.
With the Brave browser and the Nextcloud client, I was able to work around the problem by setting the following environment variables:
export XDG_CURRENT_DESKTOP=anythingelse
unset KDE_FULL_SESSION
Now I can’t set these variables globally, because some programs don’t work properly with them, or the GUI doesn’t run properly.
The korganizer (via akonadi) completely refuses to use the libsecret under Manjaro, which worked under Debian.
I’ve been looking for a solution for 3 days now, but haven’t really found one. GDM3 comes with the Gnome keyring, which I had deactivated under Debian to make it work (otherwise Debian behaved similarly).
Only with SDDM there is no GNU keyring that could be deactivated. But it still doesn’t work.
Has anyone tried this themselves and got it to work?