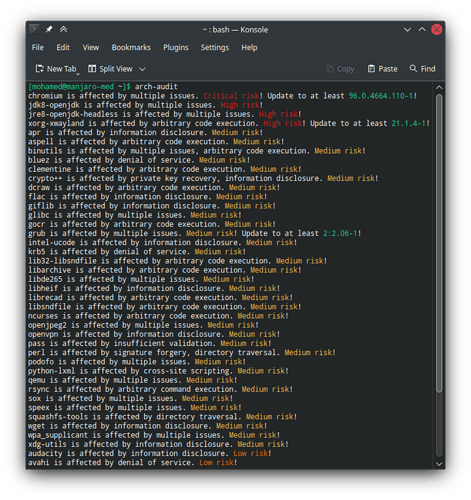
So this is the list I get with arch-audit with a not yet fully updated unstable system of Manjaro:
[phil@development community]$ arch-audit -c
jdk8-openjdk is affected by multiple issues. (CVE-2021-2388, CVE-2021-2369, CVE-2021-2341, CVE-2021-35603, CVE-2021-35588, CVE-2021-35586, CVE-2021-35578, CVE-2021-35567, CVE-2021-35565, CVE-2021-35564, CVE-2021-35561, CVE-2021-35559, CVE-2021-35556, CVE-2021-35550). High risk!
jre8-openjdk-headless is affected by multiple issues. (CVE-2021-2388, CVE-2021-2369, CVE-2021-2341, CVE-2021-35603, CVE-2021-35588, CVE-2021-35586, CVE-2021-35578, CVE-2021-35567, CVE-2021-35565, CVE-2021-35564, CVE-2021-35561, CVE-2021-35559, CVE-2021-35556, CVE-2021-35550). High risk!
openssl-1.0 is affected by multiple issues. (CVE-2021-3712, CVE-2021-3601, CVE-2021-23841, CVE-2021-23840, CVE-2021-23839, CVE-2020-1971, CVE-2020-1968). High risk!
ansible-core is affected by information disclosure. (CVE-2021-3681, CVE-2021-3620). Medium risk!
apr is affected by information disclosure. (CVE-2021-35940). Medium risk!
aspell is affected by arbitrary code execution. (CVE-2019-25051). Medium risk!
binutils is affected by multiple issues, arbitrary code execution. (CVE-2021-3648, CVE-2021-3530, CVE-2021-20197, CVE-2021-3549). Medium risk!
bluez is affected by denial of service. (CVE-2021-41229). Medium risk!
cpio is affected by arbitrary command execution. (CVE-2021-38185). Medium risk!
dcraw is affected by arbitrary code execution. (CVE-2021-3624). Medium risk!
flac is affected by information disclosure. (CVE-2021-0561). Medium risk!
giflib is affected by information disclosure. (CVE-2020-23922). Medium risk!
glibc is affected by multiple issues. (CVE-2021-43396, CVE-2021-35942, CVE-2021-33574, CVE-2021-27645). Medium risk!
grub is affected by multiple issues. (CVE-2021-20233, CVE-2021-20225, CVE-2020-27779, CVE-2020-27749, CVE-2020-25647, CVE-2020-25632, CVE-2020-14372). Medium risk! Update to at least 2:2.06-1!
krb5 is affected by denial of service. (CVE-2021-37750). Medium risk!
lib32-libsndfile is affected by arbitrary code execution. (CVE-2021-3246). Medium risk!
libarchive is affected by arbitrary code execution. (CVE-2021-36976). Medium risk!
libde265 is affected by multiple issues. (CVE-2020-21606, CVE-2020-21605, CVE-2020-21604, CVE-2020-21603, CVE-2020-21602, CVE-2020-21601, CVE-2020-21600, CVE-2020-21599, CVE-2020-21598, CVE-2020-21597, CVE-2020-21596, CVE-2020-21595, CVE-2020-21594). Medium risk!
libgrss is affected by man-in-the-middle. (CVE-2016-20011). Medium risk!
libheif is affected by information disclosure. (CVE-2020-23109). Medium risk!
libsndfile is affected by arbitrary code execution. (CVE-2021-3246). Medium risk!
linux-lts is affected by multiple issues. (CVE-2021-43976, CVE-2021-4095, CVE-2021-4028, CVE-2021-4023, CVE-2021-3847, CVE-2021-3759, CVE-2021-3752, CVE-2021-3669, CVE-2021-30178, CVE-2021-29648). Medium risk!
ncurses is affected by arbitrary code execution. (CVE-2021-39537). Medium risk!
npm is affected by insufficient validation. (CVE-2021-43616). Medium risk!
openjpeg2 is affected by multiple issues. (CVE-2021-3575, CVE-2021-29338, CVE-2019-6988, CVE-2018-20846, CVE-2018-16376). Medium risk!
openvpn is affected by information disclosure. (CVE-2021-3773). Medium risk!
perl is affected by signature forgery, directory traversal. (CVE-2020-16156, CVE-2021-36770). Medium risk!
python-lxml is affected by cross-site scripting. (CVE-2021-43818). Medium risk!
python-pip is affected by silent downgrade. (CVE-2021-3572). Medium risk!
python-reportlab is affected by url request injection. (CVE-2020-28463). Medium risk!
qemu is affected by multiple issues. (CVE-2021-3947, CVE-2021-3930, CVE-2021-3750, CVE-2021-3748, CVE-2021-3735, CVE-2021-3713, CVE-2021-3638, CVE-2021-3611, CVE-2021-3507, CVE-2021-20255, CVE-2021-20203, CVE-2021-20196, CVE-2020-15859, CVE-2020-14394). Medium risk!
rsync is affected by arbitrary command execution. (CVE-2021-3755). Medium risk!
speex is affected by multiple issues. (CVE-2020-23904, CVE-2020-23903). Medium risk!
squashfs-tools is affected by directory traversal. (CVE-2021-41072). Medium risk!
wget is affected by information disclosure. (CVE-2021-31879). Medium risk!
wpa_supplicant is affected by multiple issues. (CVE-2021-30004, CVE-2021-27803, CVE-2021-0535). Medium risk!
xdg-utils is affected by information disclosure. (CVE-2020-27748). Medium risk!
audacity is affected by information disclosure. (CVE-2020-11867). Low risk!
avahi is affected by denial of service. (CVE-2021-3468). Low risk!
imagemagick is affected by denial of service. (CVE-2021-34183). Low risk!
kexec-tools is affected by information disclosure. (CVE-2021-20269). Low risk!
lua is affected by denial of service. (CVE-2021-43519). Low risk!
lua52 is affected by denial of service. (CVE-2021-43519). Low risk!
lua53 is affected by denial of service. (CVE-2021-43519). Low risk!
openssh is affected by information disclosure. (CVE-2016-20012). Low risk!
p7zip is affected by denial of service. (CVE-2021-3465). Low risk!
A full list can be found here: https://security.archlinux.org/
grub is a false positive as we don’t use epoch for that package. Same goes for linux-lts, which we don’t ship at all. Others we have to take a look at.
Some of the problems with Arch are:
- to provide security updates we can do that downstream, however upstream will then still have the issue
- we can’t simply provide and push updated packages to Arch directly, as for example PostmarketOS developers can do to Alpine Linux
- doing anything for Arch as a packager, you have to be first a Trusted User and maybe you can get the rank as an Arch packager
We have to see on how we may improve our cooperation, as Manjaro wants to get more Beginners and Noobs to Linux, which Arch might not have on their agenda. The best thing which could happen would been that Calamares and other graphical tools would be part of Arch and Distros like us would have direct access to Arch infrastructure to improve Arch to be not so hostile to new users. Maybe a pipedream …
Also for the jdk8 problem there is a fix posted since 24 October 2021, but seems no interest yet to tackle that …