During initial startup VLC itself asks about sort of to download a file metadata from Internet or not.
I answered to disallow access.
Likely the setting is here:
$ cat /home/m/.config/vlc/vlcrc | grep -iE "metadata[- ]network[- ]access"
# Allow metadata network access (boolean)
#metadata-network-access=0
$
I changed other settings about 10-15 setting items: show toolbars, other interface-related staff, input/codecs tab: profiles, deinterlace method… but I did not touch network settings after reject access to download metadata on initial VLC start.
So, what do we have here?
$ networkctl status | grep -iv "::"
WARNING: systemd-networkd is not running, output will be incomplete.
● State: n/a
Online state: unknown
Address: 172.27.235.75 on enp1s0
Gateway: 172.27.235.73 on enp1s0
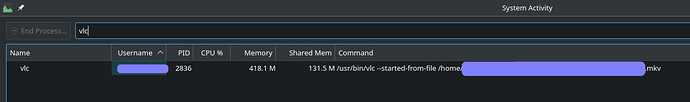
$ sudo lsof -ni | grep -i vlc | grep -i ipv4
vlc 2836 m 19u IPv4 20074 0t0 TCP 127.0.0.1:44149 (LISTEN)
vlc 2836 m 21u IPv4 20075 0t0 UDP 127.0.0.1:44149
vlc 2836 m 22u IPv4 20077 0t0 TCP 172.27.235.75:35461 (LISTEN)
vlc 2836 m 23u IPv4 20078 0t0 UDP 172.27.235.75:35461
$
command line args used (simple execution via GUI (Dolphin))
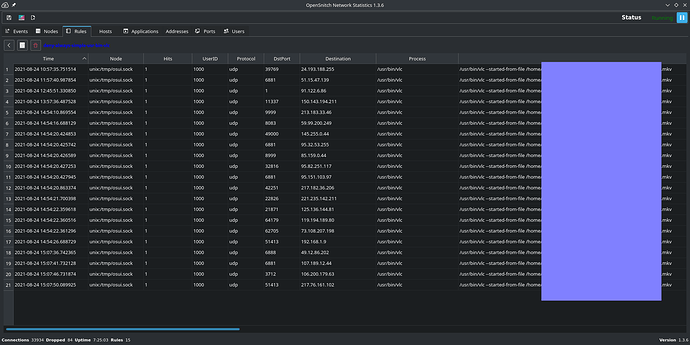
history of outbound connections (destination host list)
the `vlc` info
$ pacman -Qi vlc | grep -iv packager
Name : vlc
Version : 3.0.16-3
Description : Multi-platform MPEG, VCD/DVD, and DivX player
Architecture : x86_64
URL : https://www.videolan.org/vlc/
Licenses : LGPL2.1 GPL2
Groups : None
Provides : None
Depends On : a52dec libdvbpsi libxpm libdca libproxy lua52 libidn libmatroska taglib libmpcdec ffmpeg faad2 libmad libmpeg2 xcb-util-keysyms libtar libxinerama libsecret libupnp libixml.so=11-64 libupnp.so=17-64 libarchive qt5-base qt5-x11extras qt5-svg freetype2 fribidi harfbuzz fontconfig libxml2 gnutls libplacebo wayland-protocols
Optional Deps : avahi: service discovery using bonjour protocol [installed]
aom: AOM AV1 codec [installed]
gst-plugins-base-libs: for libgst plugins [installed]
dav1d: dav1d AV1 decoder [installed]
libdvdcss: decoding encrypted DVDs [installed]
libavc1394: devices using the 1394ta AV/C [installed]
libdc1394: IEEE 1394 access plugin [installed]
kwallet: kwallet keystore [installed]
libva-vdpau-driver: vdpau backend nvidia [installed]
libva-intel-driver: video backend intel [installed]
libbluray: Blu-Ray video input [installed]
flac: Free Lossless Audio Codec plugin [installed]
twolame: TwoLAME mpeg2 encoder plugin [installed]
libgme: Game Music Emu plugin [installed]
vcdimager: navigate VCD with libvcdinfo [installed]
libmtp: MTP devices discovery [installed]
systemd-libs: udev services discovery [installed]
smbclient: SMB access plugin [installed]
libcdio: audio CD playback [installed]
gnu-free-fonts: subtitle font
ttf-dejavu: subtitle font [installed]
libssh2: sftp access [installed]
libnfs: NFS access [installed]
mpg123: mpg123 codec [installed]
protobuf: chromecast streaming [installed]
libmicrodns: mDNS services discovery (chromecast etc) [installed]
lua52-socket: http interface
libdvdread: DVD input module [installed]
libdvdnav: DVD with navigation input module [installed]
libogg: Ogg and OggSpots codec [installed]
libshout: shoutcast/icecast output plugin [installed]
libmodplug: MOD output plugin [installed]
libvpx: VP8 and VP9 codec [installed]
libvorbis: Vorbis decoder/encoder [installed]
speex: Speex codec [installed]
opus: opus codec [installed]
libtheora: theora codec [installed]
libpng: PNG support [installed]
libjpeg-turbo: JPEG support [installed]
librsvg: SVG plugin [installed]
x264: H264 encoding [installed]
x265: HEVC/H.265 encoder [installed]
zvbi: VBI/Teletext/webcam/v4l2 capture/decoding [installed]
libass: Subtitle support [installed]
libkate: Kate codec [installed]
libtiger: Tiger rendering for Kate streams
sdl_image: SDL image support
srt: SRT input/output plugin [installed]
aalib: ASCII art video output [installed]
libcaca: colored ASCII art video output [installed]
libpulse: PulseAudio audio output [installed]
alsa-lib: ALSA audio output [installed]
jack: jack audio server [installed]
libsamplerate: audio Resampler [installed]
libsoxr: SoX audio Resampler [installed]
chromaprint: Chromaprint audio fingerprinter [installed]
lirc: lirc control [installed]
libgoom2: Goom visualization
projectm: ProjectM visualisation
ncurses: ncurses interface [installed]
libnotify: notification plugin [installed]
gtk3: notification plugin [installed]
aribb24: aribsub support
aribb25: aribcam support
pcsclite: aribcam support [installed]
Required By : elisa
Optional For : None
Conflicts With : vlc-plugin
Replaces : vlc-plugin
Installed Size : 59.77 MiB
Build Date : Wed 04 Aug 2021 11:22:58 EEST
Install Date : Mon 23 Aug 2021 17:34:54 EEST
Install Reason : Explicitly installed
Install Script : No
Validated By : Signature
$ shasum /usr/bin/vlc -a 224
ede44a86838be7923bb8dee544fb4f2887b787c70a12619938475e90 /usr/bin/vlc
$ shasum /usr/bin/vlc -a 256
5191dbd08a3895e4aad6206dfe0aa3ed6d46bc03dbc19f15312682df0b9320eb /usr/bin/vlc
$ shasum /usr/bin/vlc -a 512
6a9160ff86e3680febefa5b0a0eb84a9b779d235eac0cd7324e585660788f79adbd90f070ab2cb4e2a79a8bbe0aa0453d316867f2ed17309b356a8e6b1e13a20 /usr/bin/vlc
$
So, while the local app VLC media player playbacks a local file, it connects to Internet hosts, even many various hosts, even with metadata access turned off, even listens incoming connections.
For now I can’t figure out why.
Firewall helps (at least that simple ufw, which controls only TCP and UDP protocols, unfortunately). There are many unexpected or sophisticated (complex environment so with less predictable behavior) cases could be besides vulnerabilities and improperly / not enough configured FW on a router (if a user has a configurable firewall on a router and that user learned and configured FW there completely as he want it to be).
So you see that to have correctly configured firewall a user should properly and fully configure it on a router or (but I insist on the “and”) all user machines even in local network.
A user have to learn firewall technologies anyway: to correctly and completely setup it on a router or (much better the “and”) on every end-user machine.
Also, how do you recognize which app do listens connections or do connects to a host on a router (the connection initiator app name (and path))? You can’t. App info is absent in a network packet, and presents only: in/out status, protocol, IP/hostname, port.
Are you still on the development stage of no FW is needed on a end-user devices?
Just learn about it more and you will find useful or very useful cases (if you care of privacy of course).
Why to resist against the option for a user of defense of his/her privacy or to do not do it?
Thanks to @andreas85 and others who supports the idea (or suggests their idea to improve mine initial) and suggests their methods how to do that!
May be together we will advise some initial configuration for Manjaro (of course to ask a user to turn that initial config on or off)?
But a very basic config is ready: to block all incoming connections.
After that a user can add/remove his preferable rules. But what the point of an idea is: user will be aware about if he will agree to turn on a firewall while installation, than he will lost incoming connection to that device (only TCP and UDP protocols, not ICMP (ping)?) if leaved turned off, than that user’s privacy is more questionable subject.
Or may be a user has a perfect and completely configured (by whom? who did that configuration? who knows that user’s network usage profile? it is permanent lifetime usage profile or it can and will have changes?) router.
Again it is about a user choice: to turn it on or to do not care, the main point is aware.
Or at least just show a readme file content for a user while installation and it could point to the Firewalls - Manjaro wiki page with it’s first section of
Overview
Running a local firewall is almost always a good practice. Even when you are behind a network firewall, a local firewall protects you from threats on the inside of your network.
Thanks!