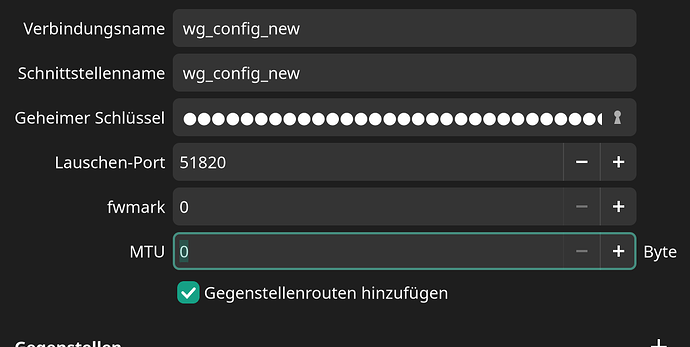
Ahh that’s what you mean, I see.
That’s all created by wg-quick when I activate my VPN connection based on the settings from here:
… which were automatically generated by FritzBox.
I dd not change anything of this configuration and have no idea what or why WireGuard is creating the iptables like it does.
I basically want to connect from a remote network to my LAN, because I need to access servers that are not reachable from the internet (which is intended).
The client configuration on my laptop (remote) is the one that I quoted. It has not changed.
The FritzBox configuration looks like this (at least that’s what the UI lets me know):
[Interface]
PrivateKey = XXX=
ListenPort = 58130
Address = 192.168.0.1/24
DNS = 192.168.0.1
DNS = fritz.box
[Peer]
PublicKey = 0atflG8Sas8Seiu5eyFTe0udcgDfgFvTUPnorcuZi3k=
PresharedKey = XXX=
AllowedIPs = 192.168.0.202/32
PersistentKeepalive = 25
[Peer]
PublicKey = LXfTVriqw/cNMIKyuK9B7RupZhyZk0LETiJ50HCfsHg=
PresharedKey = XXX=
AllowedIPs = 192.168.0.201/32
PersistentKeepalive = 25
I also wondered why there are two allowed IPs when 0.0.0.0/0 should already include everything, but that’s what FritzBox generated. I guess/ hope they have their reasons.
I have no idea what it means, but probably yes.
No I am testing it from a remote network. IIRC from within the LAN the connection was possible, but not 100% sure about this.
As far as I know, no I don’t. At least nothing active.
Actually my last statement wasn’t 100% true, because I finally managed to establish a working VPN tunnel to my FritzBox 
But it was not with WireGuard, but instead over IPSec, the other (legacy?) option that FritzBox gives you.
For some reason, in this case the connection is successful, and I can actually send data/ ping / reach my internal websites.
This makes debugging a lot easier, because I don’t need to call my family members at home to test a setting/ get some logs  .
.
So it’s by far not as critical anymore, but it would be nice to know why my IPSec configuration is working, but my Wireguard one isn’t.
Here is the IP configuration for IPSec:
ip addr ✔
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
3: wlp0s20f3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 34:7d:f6:8e:6e:a3 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.58/24 brd 192.168.1.255 scope global dynamic noprefixroute wlp0s20f3
valid_lft 597447sec preferred_lft 597447sec
inet6 fe80::55ba:ff3b:a12b:5901/64 scope link noprefixroute
valid_lft forever preferred_lft forever
4: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:1b:79:e3 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
6: br-b70272889e99: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:73:32:5f:b6 brd ff:ff:ff:ff:ff:ff
inet 172.26.1.1/24 brd 172.26.1.255 scope global br-b70272889e99
valid_lft forever preferred_lft forever
7: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:c5:fe:e3:31 brd ff:ff:ff:ff:ff:ff
inet 172.26.0.1/24 brd 172.26.0.255 scope global docker0
valid_lft forever preferred_lft forever
19: enp0s13f0u1u4: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel state DOWN group default qlen 1000
link/ether 00:e0:4c:68:05:d1 brd ff:ff:ff:ff:ff:ff
34: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1412 qdisc fq_codel state UNKNOWN group default qlen 500
link/none
inet 192.168.0.203/24 brd 192.168.0.255 scope global noprefixroute tun0
valid_lft forever preferred_lft forever
inet6 fe80::12be:9690:bd7c:145c/64 scope link stable-privacy proto kernel_ll
valid_lft forever preferred_lft forever
And here for WireGuard:
ip addr PIPE ✘ 3m 33s
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
3: wlp0s20f3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 34:7d:f6:8e:6e:a3 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.58/24 brd 192.168.1.255 scope global dynamic noprefixroute wlp0s20f3
valid_lft 597539sec preferred_lft 597539sec
inet6 fe80::55ba:ff3b:a12b:5901/64 scope link noprefixroute
valid_lft forever preferred_lft forever
4: virbr0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether 52:54:00:1b:79:e3 brd ff:ff:ff:ff:ff:ff
inet 192.168.122.1/24 brd 192.168.122.255 scope global virbr0
valid_lft forever preferred_lft forever
6: br-b70272889e99: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:73:32:5f:b6 brd ff:ff:ff:ff:ff:ff
inet 172.26.1.1/24 brd 172.26.1.255 scope global br-b70272889e99
valid_lft forever preferred_lft forever
7: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN group default
link/ether 02:42:c5:fe:e3:31 brd ff:ff:ff:ff:ff:ff
inet 172.26.0.1/24 brd 172.26.0.255 scope global docker0
valid_lft forever preferred_lft forever
19: enp0s13f0u1u4: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc fq_codel state DOWN group default qlen 1000
link/ether 00:e0:4c:68:05:d1 brd ff:ff:ff:ff:ff:ff
32: wg_config: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
link/none
inet 192.168.0.201/24 brd 192.168.0.255 scope global noprefixroute wg_config
valid_lft forever preferred_lft forever