Not a single entry for crypttab, and you read it with root privleges?
Does this file exist on your system:
ls -lh /crypto_keyfile.bin
Grub always prompted for a passphrase? Even before you destroyed LUKS key slot 1?
I thought you switched to systemd-boot, because of how slow Grub is at decrypting the key? What happens if you try with systemd-boot now, after having destroyed the extra key slot?
Systemd-boot was retrieving the key file from somewhere if you could decrypt without your passphrase.
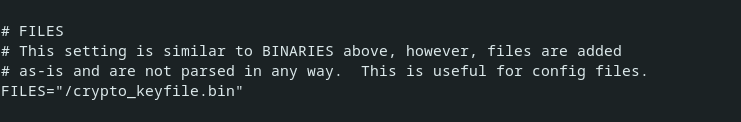
Last place I would look is under /etc/mkinitcpio.conf
Look for a line that reads
FILES=“/crypto_keyfile.bin”
If such a line exists, comment it out or remove it.
What this does is load the key file into the initramfs (like a “mini” filesystem that lives and runs in RAM), and so the boot-loader has a filesystem it can work with and retrieve files, if needed, before you get access to the real root filesystem.
Commenting out the above line and removing the file /crypto_keyfile.bin should remove any traces of this behavior.
Don’t forget to rebuild and update.
sudo mkinitcpio -P
sudo grub-install
sudo update-grub
Also check out systemd-boot config:
sudo bootctl list
Alternatively, check the config file(s) under the folder “[esp]/loader/entries/” in your EFI system partition.
UPDATE: I’m not sure if you decided to switch back to Grub or still continue to use systemd-boot?
 (How can the bootloader retrieve the key to unlock the container when the container needs to be unlocked to retrieve the key?!)
(How can the bootloader retrieve the key to unlock the container when the container needs to be unlocked to retrieve the key?!)