It’s true that a 177kB pic uses same space as a 30k-word novella. But considering that most drives these days are over 1,000,000,000kB, the importance of that fact is somewhat diluted.
Doesn’t capture interesting non-text tidbits.
Good point. Touché. Ok, I’ll try to limit use of pics when text will work.
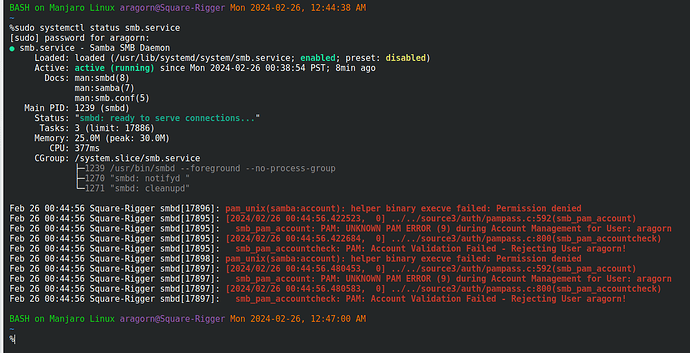
Lemme check… yep, installed and loaded. However, it’s also installed and loaded on my main computer, but it doesn’t have this problem. Let me check some configuration files…
Oops, I can’t check any configuration files, even as root! What the devil??? What’s up with permissions on “/etc”??? Lemme do “la -al” on “/”… Ewww… what the heck is up with this mess???
drwxr-xr-x 20 root root 4096 2024-02-21 20:12 ./
drwxr-xr-x 20 root root 4096 2024-02-21 20:12 ../
lrwxrwxrwx 1 root root 7 2024-01-19 10:16 bin -> usr/bin/
drwxr-xr-x 5 root root 4096 2024-05-05 14:43 boot/
drwxr-xr-x 4 root root 4096 2022-04-04 13:12 .config/
drwxr-xr-x 19 root root 4680 2024-05-07 15:56 dev/
d-wx--x--x 151 root root 12288 2024-05-07 15:25 etc/
drwxr-xr-x 7 root root 4096 2022-11-28 20:25 home/
lrwxrwxrwx 1 root root 7 2024-01-19 10:16 lib -> usr/lib/
lrwxrwxrwx 1 root root 7 2024-01-19 10:16 lib64 -> usr/lib/
d-wx------ 2 root root 16384 2022-01-27 11:44 lost+found/
d-wx--x--x 5 root root 4096 2022-02-04 02:47 media/
d-wx--x--x 3 root root 4096 2022-11-14 18:04 mnt/
d-wx--x--x 8 root root 4096 2023-04-18 18:54 opt/
dr-xr-xr-x 300 root root 0 2024-05-07 14:53 proc/
d-wx--x--- 20 root root 4096 2024-05-07 15:54 root/
drwxr-xr-x 37 root root 940 2024-05-07 15:00 run/
lrwxrwxrwx 1 root root 7 2024-01-19 10:16 sbin -> usr/bin/
d-wx-wx-wx 2 aragorn aragorn 4096 2022-11-05 07:15 share/
lrwxrwxrwx 1 root root 20 2022-09-16 21:33 snap -> /var/lib/snapd/snap//
drwxr-xr-x 5 root root 4096 2022-02-06 18:10 srv/
dr-xr-xr-x 13 root root 0 2024-05-07 14:53 sys/
drwxrwxrwt 19 root root 560 2024-05-07 15:36 tmp/
drwxr-xr-x 12 root root 4096 2024-05-07 15:25 usr/
drwxr-xr-x 13 root root 4096 2024-05-07 14:53 var/
--w------- 1 root root 19449 2021-09-07 09:35 desktopfs-pkgs.txt
-rw-r--r-- 1 root root 8 2021-09-07 09:35 .manjaro-tools
--w------- 1 root root 4952 2021-09-07 09:29 rootfs-pkgs.txt
Wow, lots of errors there! Even root is prohibited from reading “etc”, “lost+found”, “media”, “mnt”, “opt”, “root”, “share”. And “media” and “share” aren’t even supposed to be there!
Ok, I fixed the permissions errors (with many uses of “sudo chmod 0755 xxxxx”). I moved “media” back inside “/run” where it belongs. And “share” turned out to contain only an old 5.15 Linux kernel ISO file from 2022 so I just erased that. Let me restart system…
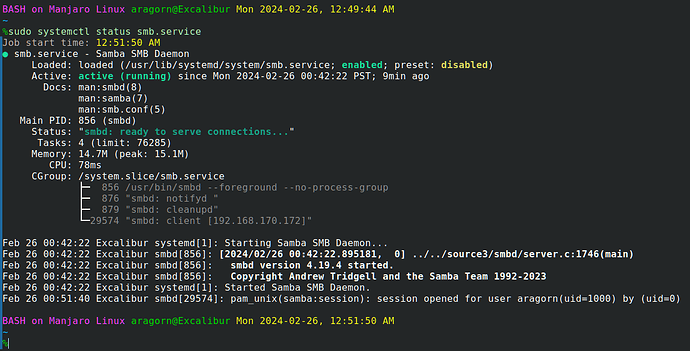
Ok, on restart, problem is fixed! Excalibur (my main computer) can now access shares on Square-Rigger (the computer that was having the sharing problems).
As for how the permissions got screwed-up, I have no clue. That’s not something I would do. And I don’t think the OS would do that. And most software doesn’t have permission to do that because the affected directories are owned by root. So apparently some piece of software with elevated permissions did it. Who when how where why, I have no idea; colour me puzzled. But for now it’s fixed. Hopefully this was a one-time fluke.