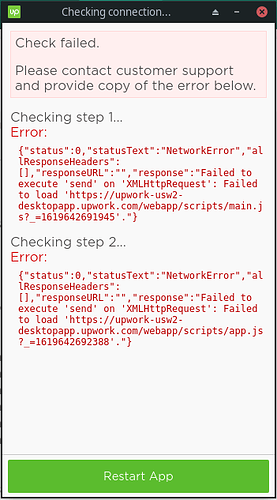
I already suggested that method - further up …
Doesn’t work either, it seems.
I thought he was set on doing it via curl for some reason.
Now I’m pretty sure it’s not OpenSSL or GnuTLS that’s buggy here. The fact that others could access the server find (me included) implies that there may be some network equipment on the way from your computer to the server that might be causing this.
Can you run openssl s_client -host upwork-usw2-desktopapp.upwork.com -port 443 -debug -msg?
I do not know anything about networking, im just a developer.
So when you talk about faulty networking equipment u’ll have to tell me wheather you’re talking about my Router or my ISP.
EDIT
[chawila@devTool ~]$ openssl s_client -host upwork-usw2-desktopapp.upwork.com -port 443 -debug -msg
CONNECTED(00000003)
>>> ??? [length 0005]
16 03 01 01 4a
>>> TLS 1.3, Handshake [length 014a], ClientHello
01 00 01 46 03 03 68 f3 97 3e 90 1e 21 c6 55 df
c7 e2 dd 84 ee c1 95 b6 04 95 91 44 ab ee 74 f7
26 76 29 35 13 a4 20 7f cc 4d 71 15 27 c6 b8 0a
28 3a eb 62 4f dc ab 30 fa ef 21 2a b4 ac ad 68
37 8d dd 59 f4 86 d1 00 3e 13 02 13 03 13 01 c0
2c c0 30 00 9f cc a9 cc a8 cc aa c0 2b c0 2f 00
9e c0 24 c0 28 00 6b c0 23 c0 27 00 67 c0 0a c0
14 00 39 c0 09 c0 13 00 33 00 9d 00 9c 00 3d 00
3c 00 35 00 2f 00 ff 01 00 00 bf 00 00 00 26 00
24 00 00 21 75 70 77 6f 72 6b 2d 75 73 77 32 2d
64 65 73 6b 74 6f 70 61 70 70 2e 75 70 77 6f 72
6b 2e 63 6f 6d 00 0b 00 04 03 00 01 02 00 0a 00
0c 00 0a 00 1d 00 17 00 1e 00 19 00 18 00 23 00
00 00 16 00 00 00 17 00 00 00 0d 00 30 00 2e 04
03 05 03 06 03 08 07 08 08 08 09 08 0a 08 0b 08
04 08 05 08 06 04 01 05 01 06 01 03 03 02 03 03
01 02 01 03 02 02 02 04 02 05 02 06 02 00 2b 00
09 08 03 04 03 03 03 02 03 01 00 2d 00 02 01 01
00 33 00 26 00 24 00 1d 00 20 b0 c6 08 07 96 97
57 e8 99 73 17 a4 38 6d 56 03 98 69 fe 88 47 9e
4a 3b 1e 3c 72 14 14 6c 33 6c
write to 0x555dc5b7a700 [0x555dc5b994f0] (335 bytes => 335 (0x14F))
0000 - 16 03 01 01 4a 01 00 01-46 03 03 68 f3 97 3e 90 ....J...F..h..>.
0010 - 1e 21 c6 55 df c7 e2 dd-84 ee c1 95 b6 04 95 91 .!.U............
0020 - 44 ab ee 74 f7 26 76 29-35 13 a4 20 7f cc 4d 71 D..t.&v)5.. ..Mq
0030 - 15 27 c6 b8 0a 28 3a eb-62 4f dc ab 30 fa ef 21 .'...(:.bO..0..!
0040 - 2a b4 ac ad 68 37 8d dd-59 f4 86 d1 00 3e 13 02 *...h7..Y....>..
0050 - 13 03 13 01 c0 2c c0 30-00 9f cc a9 cc a8 cc aa .....,.0........
0060 - c0 2b c0 2f 00 9e c0 24-c0 28 00 6b c0 23 c0 27 .+./...$.(.k.#.'
0070 - 00 67 c0 0a c0 14 00 39-c0 09 c0 13 00 33 00 9d .g.....9.....3..
0080 - 00 9c 00 3d 00 3c 00 35-00 2f 00 ff 01 00 00 bf ...=.<.5./......
0090 - 00 00 00 26 00 24 00 00-21 75 70 77 6f 72 6b 2d ...&.$..!upwork-
00a0 - 75 73 77 32 2d 64 65 73-6b 74 6f 70 61 70 70 2e usw2-desktopapp.
00b0 - 75 70 77 6f 72 6b 2e 63-6f 6d 00 0b 00 04 03 00 upwork.com......
00c0 - 01 02 00 0a 00 0c 00 0a-00 1d 00 17 00 1e 00 19 ................
00d0 - 00 18 00 23 00 00 00 16-00 00 00 17 00 00 00 0d ...#............
00e0 - 00 30 00 2e 04 03 05 03-06 03 08 07 08 08 08 09 .0..............
00f0 - 08 0a 08 0b 08 04 08 05-08 06 04 01 05 01 06 01 ................
0100 - 03 03 02 03 03 01 02 01-03 02 02 02 04 02 05 02 ................
0110 - 06 02 00 2b 00 09 08 03-04 03 03 03 02 03 01 00 ...+............
0120 - 2d 00 02 01 01 00 33 00-26 00 24 00 1d 00 20 b0 -.....3.&.$... .
0130 - c6 08 07 96 97 57 e8 99-73 17 a4 38 6d 56 03 98 .....W..s..8mV..
0140 - 69 fe 88 47 9e 4a 3b 1e-3c 72 14 14 6c 33 6c i..G.J;.<r..l3l
read from 0x555dc5b7a700 [0x555dc5b902d3] (5 bytes => 0 (0x0))
write:errno=0
---
no peer certificate available
---
No client certificate CA names sent
---
SSL handshake has read 0 bytes and written 335 bytes
Verification: OK
---
New, (NONE), Cipher is (NONE)
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
read from 0x555dc5b7a700 [0x555dc5ac81c0] (8192 bytes => 0 (0x0))
Ok, here is the text file:
It’s hard to say, could be either.
This is odd, as in my case, I get
read from 0x55c1921c3700 [0x55c1921d9303] (5 bytes => 5 (0x5))
Note the difference. The read on your side returns 0, while on my side it returns 5. 0 indicates the end of the connection. It seems for some reason the TCP connection is being terminated.
Please start sudo tcpdump port 443 in one terminal, then very quickly after that run curl https://upwork-usw2-desktopapp.upwork.com/webapp/scripts/main.js > /dev/null in a different terminal, after curl has stopped, go back to the first one, and stop tcpdump by pressing control+c.
sudo tcpdump port 443
command not found
EDIT
Installing it
Looks like you’re blocked and the server doesn’t want to talk to you.
@moson why would upwork block me. And i’m not using a static IP.
@pobrn Not sure if i’ve captured the right packets:
[chawila@devTool Desktop]$ sudo tcpdump port 443
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on enp2s0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
21:52:05.199114 IP devTool.38338 > ec2-3-7-194-106.ap-south-1.compute.amazonaws.com.https: Flags [P.], seq 2664710080:2664710134, ack 2013917673, win 1248, options [nop,nop,TS val 2680018489 ecr 486392865], length 54
21:52:05.707529 IP ec2-3-7-194-106.ap-south-1.compute.amazonaws.com.https > devTool.38338: Flags [.], ack 54, win 17, options [nop,nop,TS val 486395057 ecr 2680018489], length 0
21:52:05.707531 IP ec2-3-7-194-106.ap-south-1.compute.amazonaws.com.https > devTool.38338: Flags [P.], seq 1:57, ack 54, win 17, options [nop,nop,TS val 486395057 ecr 2680018489], length 56
21:52:05.707597 IP devTool.38338 > ec2-3-7-194-106.ap-south-1.compute.amazonaws.com.https: Flags [.], ack 57, win 1248, options [nop,nop,TS val 2680018997 ecr 486395057], length 0
21:52:06.086583 IP devTool.50920 > 149.154.167.91.https: Flags [P.], seq 2543544883:2543545020, ack 2419326864, win 502, options [nop,nop,TS val 4283832406 ecr 293753586], length 137
21:52:06.356532 IP 149.154.167.91.https > devTool.50920: Flags [P.], seq 1:154, ack 137, win 7508, options [nop,nop,TS val 293763093 ecr 4283832406], length 153
21:52:06.356584 IP devTool.50920 > 149.154.167.91.https: Flags [.], ack 154, win 501, options [nop,nop,TS val 4283832676 ecr 293763093], length 0
21:52:06.363040 IP 149.154.167.91.https > devTool.50920: Flags [P.], seq 154:243, ack 137, win 7508, options [nop,nop,TS val 293763094 ecr 4283832406], length 89
21:52:06.363072 IP devTool.50920 > 149.154.167.91.https: Flags [.], ack 243, win 501, options [nop,nop,TS val 4283832683 ecr 293763094], length 0
21:52:07.386242 IP devTool.48550 > jnb02s03-in-f4.1e100.net.https: Flags [P.], seq 2047872221:2047872260, ack 2192216213, win 501, options [nop,nop,TS val 3733080561 ecr 2785447257], length 39
21:52:07.452061 IP jnb02s03-in-f4.1e100.net.https > devTool.48550: Flags [P.], seq 1:40, ack 39, win 271, options [nop,nop,TS val 2785506256 ecr 3733080561], length 39
21:52:07.452118 IP devTool.48550 > jnb02s03-in-f4.1e100.net.https: Flags [.], ack 40, win 501, options [nop,nop,TS val 3733080627 ecr 2785506256], length 0
^C21:52:09.274252 IP devTool.60068 > 146.112.56.190.https: Flags [S], seq 4023276737, win 64240, options [mss 1460,sackOK,TS val 408015445 ecr 0,nop,wscale 7], length 0
13 packets captured
22 packets received by filter
1 packet dropped by kernel
Can you do it again, but this time run sudo tcpdump -n port 443? The name resolution causes packets to be dropped.
@pobrn so many things here:
[chawila@devTool Desktop]$ sudo tcpdump -n port 443
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on enp2s0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
21:57:01.600077 IP 192.168.0.195.42322 > 146.112.56.139.443: Flags [S], seq 3927930690, win 64240, options [mss 1460,sackOK,TS val 494959381 ecr 0,nop,wscale 7], length 0
21:57:01.800946 IP 192.168.0.195.60092 > 146.112.56.190.443: Flags [S], seq 3210946889, win 64240, options [mss 1460,sackOK,TS val 408307972 ecr 0,nop,wscale 7], length 0
21:57:01.817632 IP 146.112.56.139.443 > 192.168.0.195.42322: Flags [S.], seq 4278618918, ack 3927930691, win 43648, options [mss 1400,sackOK,TS val 2312059547 ecr 494959381,nop,wscale 9], length 0
21:57:01.817664 IP 192.168.0.195.42322 > 146.112.56.139.443: Flags [.], ack 1, win 502, options [nop,nop,TS val 494959598 ecr 2312059547], length 0
21:57:01.822923 IP 192.168.0.195.42322 > 146.112.56.139.443: Flags [P.], seq 1:518, ack 1, win 502, options [nop,nop,TS val 494959604 ecr 2312059547], length 517
21:57:02.027914 IP 146.112.56.139.443 > 192.168.0.195.42322: Flags [F.], seq 1, ack 1, win 86, options [nop,nop,TS val 2312059764 ecr 494959598], length 0
21:57:02.029608 IP 192.168.0.195.42322 > 146.112.56.139.443: Flags [F.], seq 518, ack 2, win 502, options [nop,nop,TS val 494959810 ecr 2312059764], length 0
21:57:02.032894 IP 146.112.56.190.443 > 192.168.0.195.60092: Flags [S.], seq 1232520704, ack 3210946890, win 43648, options [mss 1400,sackOK,TS val 1719002464 ecr 408307972,nop,wscale 9], length 0
21:57:02.032933 IP 192.168.0.195.60092 > 146.112.56.190.443: Flags [R], seq 3210946890, win 0, length 0
21:57:02.239971 IP 146.112.56.139.443 > 192.168.0.195.42322: Flags [R], seq 4278618920, win 0, length 0
21:57:05.199448 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [P.], seq 2664712673:2664712727, ack 2013920845, win 1309, options [nop,nop,TS val 2680318489 ecr 486467910], length 54
21:57:05.287955 IP 135.181.38.249.443 > 192.168.0.195.38920: Flags [P.], seq 4239949044:4239949082, ack 3965199920, win 1597, options [nop,nop,TS val 1473672873 ecr 1705119233], length 38
21:57:05.287955 IP 135.181.38.249.443 > 192.168.0.195.38920: Flags [P.], seq 38:69, ack 1, win 1597, options [nop,nop,TS val 1473672873 ecr 1705119233], length 31
21:57:05.287986 IP 192.168.0.195.38920 > 135.181.38.249.443: Flags [.], ack 38, win 1128, options [nop,nop,TS val 1705134608 ecr 1473672873], length 0
21:57:05.287992 IP 192.168.0.195.38920 > 135.181.38.249.443: Flags [.], ack 69, win 1128, options [nop,nop,TS val 1705134608 ecr 1473672873], length 0
21:57:05.398312 IP 192.168.0.195.38920 > 135.181.38.249.443: Flags [P.], seq 1:106, ack 69, win 1131, options [nop,nop,TS val 1705134718 ecr 1473672873], length 105
21:57:05.398329 IP 192.168.0.195.38920 > 135.181.38.249.443: Flags [P.], seq 106:649, ack 69, win 1131, options [nop,nop,TS val 1705134718 ecr 1473672873], length 543
21:57:05.667889 IP 135.181.38.249.443 > 192.168.0.195.38920: Flags [P.], seq 69:104, ack 106, win 1597, options [nop,nop,TS val 1473673253 ecr 1705134718], length 35
21:57:05.667952 IP 192.168.0.195.38920 > 135.181.38.249.443: Flags [.], ack 104, win 1131, options [nop,nop,TS val 1705134988 ecr 1473673253], length 0
21:57:05.693958 IP 135.181.38.249.443 > 192.168.0.195.38920: Flags [P.], seq 104:435, ack 649, win 1597, options [nop,nop,TS val 1473673280 ecr 1705134718], length 331
21:57:05.694016 IP 192.168.0.195.38920 > 135.181.38.249.443: Flags [.], ack 435, win 1129, options [nop,nop,TS val 1705135014 ecr 1473673280], length 0
21:57:05.708524 IP 3.7.194.106.443 > 192.168.0.195.38338: Flags [.], ack 54, win 17, options [nop,nop,TS val 486470055 ecr 2680318489], length 0
21:57:05.708526 IP 3.7.194.106.443 > 192.168.0.195.38338: Flags [P.], seq 1:57, ack 54, win 17, options [nop,nop,TS val 486470055 ecr 2680318489], length 56
21:57:05.708591 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [.], ack 57, win 1309, options [nop,nop,TS val 2680318998 ecr 486470055], length 0
21:57:09.781611 IP 192.168.0.195.37338 > 13.235.147.72.443: Flags [F.], seq 1946630571, ack 2671129146, win 501, options [nop,nop,TS val 2160409447 ecr 238176317], length 0
21:57:09.781658 IP 192.168.0.195.37334 > 13.235.147.72.443: Flags [F.], seq 1270808210, ack 3936144402, win 501, options [nop,nop,TS val 2160409447 ecr 227378373], length 0
21:57:09.861099 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [S], seq 3382446468, win 64240, options [mss 1460,sackOK,TS val 1806616939 ecr 0,nop,wscale 7], length 0
21:57:09.896758 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [S.], seq 2176535575, ack 3382446469, win 65535, options [mss 1400,sackOK,TS val 2751895944 ecr 1806616939,nop,wscale 9], length 0
21:57:09.896849 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 1, win 502, options [nop,nop,TS val 1806616975 ecr 2751895944], length 0
21:57:09.897379 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [P.], seq 1:518, ack 1, win 502, options [nop,nop,TS val 1806616975 ecr 2751895944], length 517
21:57:09.939768 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [.], ack 518, win 131, options [nop,nop,TS val 2751895987 ecr 1806616975], length 0
21:57:09.941754 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [.], seq 1:1389, ack 518, win 131, options [nop,nop,TS val 2751895988 ecr 1806616975], length 1388
21:57:09.941801 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 1389, win 501, options [nop,nop,TS val 1806617019 ecr 2751895988], length 0
21:57:09.941839 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [P.], seq 1389:2777, ack 518, win 131, options [nop,nop,TS val 2751895988 ecr 1806616975], length 1388
21:57:09.941859 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 2777, win 497, options [nop,nop,TS val 1806617020 ecr 2751895988], length 0
21:57:09.941934 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [P.], seq 2777:4032, ack 518, win 131, options [nop,nop,TS val 2751895989 ecr 1806616975], length 1255
21:57:09.941950 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 4032, win 490, options [nop,nop,TS val 1806617020 ecr 2751895989], length 0
21:57:09.942976 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [P.], seq 518:582, ack 4032, win 501, options [nop,nop,TS val 1806617021 ecr 2751895989], length 64
21:57:09.943286 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [P.], seq 582:674, ack 4032, win 501, options [nop,nop,TS val 1806617021 ecr 2751895989], length 92
21:57:09.943699 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [P.], seq 674:1373, ack 4032, win 501, options [nop,nop,TS val 1806617021 ecr 2751895989], length 699
21:57:09.982869 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [.], ack 582, win 131, options [nop,nop,TS val 2751896030 ecr 1806617021], length 0
21:57:09.982870 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [P.], seq 4032:4094, ack 582, win 131, options [nop,nop,TS val 2751896030 ecr 1806617021], length 62
21:57:09.982941 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 4094, win 501, options [nop,nop,TS val 1806617061 ecr 2751896030], length 0
21:57:09.983232 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [P.], seq 1373:1404, ack 4094, win 501, options [nop,nop,TS val 1806617061 ecr 2751896030], length 31
21:57:09.986489 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [.], ack 674, win 131, options [nop,nop,TS val 2751896033 ecr 1806617021], length 0
21:57:09.986490 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [P.], seq 4094:4125, ack 674, win 131, options [nop,nop,TS val 2751896033 ecr 1806617021], length 31
21:57:09.986558 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 4125, win 501, options [nop,nop,TS val 1806617064 ecr 2751896033], length 0
21:57:09.986596 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [.], ack 1373, win 133, options [nop,nop,TS val 2751896033 ecr 1806617021], length 0
21:57:10.025493 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [.], ack 1404, win 133, options [nop,nop,TS val 2751896072 ecr 1806617061], length 0
21:57:10.221594 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [P.], seq 4125:4555, ack 1404, win 133, options [nop,nop,TS val 2751896269 ecr 1806617061], length 430
21:57:10.221595 IP 52.85.183.57.443 > 192.168.0.195.56276: Flags [P.], seq 4555:4586, ack 1404, win 133, options [nop,nop,TS val 2751896269 ecr 1806617061], length 31
21:57:10.221616 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 4555, win 501, options [nop,nop,TS val 1806617299 ecr 2751896269], length 0
21:57:10.221631 IP 192.168.0.195.56276 > 52.85.183.57.443: Flags [.], ack 4586, win 501, options [nop,nop,TS val 1806617299 ecr 2751896269], length 0
21:57:11.007541 IP 192.168.0.195.37334 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160410673 ecr 227378373], length 0
21:57:11.007563 IP 192.168.0.195.37338 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160410673 ecr 238176317], length 0
21:57:11.471055 IP 3.7.194.106.443 > 192.168.0.195.38338: Flags [P.], seq 57:728, ack 54, win 17, options [nop,nop,TS val 486471498 ecr 2680318998], length 671
21:57:11.471085 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [.], ack 728, win 1329, options [nop,nop,TS val 2680324761 ecr 486471498], length 0
21:57:12.420880 IP 192.168.0.195.37338 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160412087 ecr 238176317], length 0
21:57:12.420887 IP 192.168.0.195.37334 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160412087 ecr 227378373], length 0
21:57:13.637902 IP 135.181.38.249.443 > 192.168.0.195.40834: Flags [P.], seq 1848587792:1848587830, ack 3656906169, win 501, options [nop,nop,TS val 1473681223 ecr 1705118247], length 38
21:57:13.637903 IP 135.181.38.249.443 > 192.168.0.195.40834: Flags [P.], seq 38:69, ack 1, win 501, options [nop,nop,TS val 1473681223 ecr 1705118247], length 31
21:57:13.637934 IP 192.168.0.195.40834 > 135.181.38.249.443: Flags [.], ack 38, win 501, options [nop,nop,TS val 1705142958 ecr 1473681223], length 0
21:57:13.637940 IP 192.168.0.195.40834 > 135.181.38.249.443: Flags [.], ack 69, win 501, options [nop,nop,TS val 1705142958 ecr 1473681223], length 0
21:57:15.199467 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [P.], seq 54:108, ack 728, win 1329, options [nop,nop,TS val 2680328489 ecr 486471498], length 54
21:57:15.274207 IP 192.168.0.195.37334 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160414940 ecr 227378373], length 0
21:57:15.274225 IP 192.168.0.195.37338 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160414940 ecr 238176317], length 0
21:57:15.707839 IP 3.7.194.106.443 > 192.168.0.195.38338: Flags [P.], seq 728:784, ack 108, win 17, options [nop,nop,TS val 486472556 ecr 2680328489], length 56
21:57:15.707895 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [.], ack 784, win 1329, options [nop,nop,TS val 2680328998 ecr 486472556], length 0
21:57:16.603322 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [P.], seq 108:164, ack 784, win 1329, options [nop,nop,TS val 2680329893 ecr 486472556], length 56
21:57:16.656446 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [P.], seq 164:286, ack 784, win 1329, options [nop,nop,TS val 2680329946 ecr 486472556], length 122
21:57:16.692662 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [S], seq 895200064, win 64240, options [mss 1460,sackOK,TS val 2160416358 ecr 0,nop,wscale 7], length 0
21:57:16.913267 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [S], seq 2971317761, win 64240, options [mss 1460,sackOK,TS val 2160416579 ecr 0,nop,wscale 7], length 0
21:57:17.140033 IP 3.7.194.106.443 > 192.168.0.195.38338: Flags [.], ack 164, win 17, options [nop,nop,TS val 486472914 ecr 2680329893], length 0
21:57:17.152925 IP 3.7.194.106.443 > 192.168.0.195.38338: Flags [.], ack 286, win 17, options [nop,nop,TS val 486472917 ecr 2680329946], length 0
21:57:17.152968 IP 3.7.194.106.443 > 192.168.0.195.38338: Flags [P.], seq 784:919, ack 286, win 17, options [nop,nop,TS val 486472917 ecr 2680329946], length 135
21:57:17.152991 IP 192.168.0.195.38338 > 3.7.194.106.443: Flags [.], ack 919, win 1349, options [nop,nop,TS val 2680330443 ecr 486472917], length 0
21:57:17.176012 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [S.], seq 2014510617, ack 895200065, win 32200, options [mss 1300,sackOK,TS val 270623655 ecr 2160416358,nop,wscale 12], length 0
21:57:17.176088 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 1, win 502, options [nop,nop,TS val 2160416842 ecr 270623655], length 0
21:57:17.176582 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [P.], seq 1:518, ack 1, win 502, options [nop,nop,TS val 2160416842 ecr 270623655], length 517
21:57:17.440890 IP 13.235.147.72.443 > 192.168.0.195.37358: Flags [S.], seq 185177248, ack 2971317762, win 32200, options [mss 1300,sackOK,TS val 76219399 ecr 2160416579,nop,wscale 12], length 0
21:57:17.440923 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [.], ack 1, win 502, options [nop,nop,TS val 2160417107 ecr 76219399], length 0
21:57:17.441097 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [P.], seq 1:518, ack 1, win 502, options [nop,nop,TS val 2160417107 ecr 76219399], length 517
21:57:17.702790 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [.], seq 1289:2577, ack 518, win 9, options [nop,nop,TS val 270623779 ecr 2160416842], length 1288
21:57:17.702849 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 1, win 502, options [nop,nop,TS val 2160417369 ecr 270623655,nop,nop,sack 1 {1289:2577}], length 0
21:57:17.702867 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [P.], seq 2577:3553, ack 518, win 9, options [nop,nop,TS val 270623779 ecr 2160416842], length 976
21:57:17.702881 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 1, win 502, options [nop,nop,TS val 2160417369 ecr 270623655,nop,nop,sack 1 {1289:3553}], length 0
21:57:17.702957 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [.], seq 1:1289, ack 518, win 9, options [nop,nop,TS val 270623779 ecr 2160416842], length 1288
21:57:17.702997 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 3553, win 492, options [nop,nop,TS val 2160417369 ecr 270623779], length 0
21:57:17.704071 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [P.], seq 518:582, ack 3553, win 501, options [nop,nop,TS val 2160417370 ecr 270623779], length 64
21:57:17.704426 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [P.], seq 582:674, ack 3553, win 501, options [nop,nop,TS val 2160417370 ecr 270623779], length 92
21:57:17.704872 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [P.], seq 674:1219, ack 3553, win 501, options [nop,nop,TS val 2160417371 ecr 270623779], length 545
21:57:17.704955 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [P.], seq 1219:1427, ack 3553, win 501, options [nop,nop,TS val 2160417371 ecr 270623779], length 208
21:57:17.979832 IP 13.235.147.72.443 > 192.168.0.195.37358: Flags [.], seq 1289:2577, ack 518, win 9, options [nop,nop,TS val 76219528 ecr 2160417107], length 1288
21:57:17.979891 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [.], ack 1, win 502, options [nop,nop,TS val 2160417646 ecr 76219399,nop,nop,sack 1 {1289:2577}], length 0
21:57:17.979910 IP 13.235.147.72.443 > 192.168.0.195.37358: Flags [.], seq 1:1289, ack 518, win 9, options [nop,nop,TS val 76219528 ecr 2160417107], length 1288
21:57:17.979948 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [.], ack 2577, win 497, options [nop,nop,TS val 2160417646 ecr 76219528], length 0
21:57:17.979962 IP 13.235.147.72.443 > 192.168.0.195.37358: Flags [P.], seq 2577:3553, ack 518, win 9, options [nop,nop,TS val 76219528 ecr 2160417107], length 976
21:57:17.979977 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [.], ack 3553, win 492, options [nop,nop,TS val 2160417646 ecr 76219528], length 0
21:57:17.981111 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [P.], seq 518:582, ack 3553, win 501, options [nop,nop,TS val 2160417647 ecr 76219528], length 64
21:57:18.363055 IP 192.168.0.195.40834 > 135.181.38.249.443: Flags [P.], seq 1:94, ack 69, win 501, options [nop,nop,TS val 1705147683 ecr 1473681223], length 93
21:57:18.363139 IP 192.168.0.195.40834 > 135.181.38.249.443: Flags [P.], seq 94:368, ack 69, win 501, options [nop,nop,TS val 1705147683 ecr 1473681223], length 274
21:57:18.418088 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [P.], seq 3808:4079, ack 674, win 9, options [nop,nop,TS val 270623909 ecr 2160417370], length 271
21:57:18.418088 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [P.], seq 4079:4125, ack 674, win 9, options [nop,nop,TS val 270623909 ecr 2160417370], length 46
21:57:18.418116 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 3553, win 501, options [nop,nop,TS val 2160418084 ecr 270623779,nop,nop,sack 1 {3808:4079}], length 0
21:57:18.418121 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 3553, win 501, options [nop,nop,TS val 2160418084 ecr 270623779,nop,nop,sack 1 {3808:4125}], length 0
21:57:18.418148 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [P.], seq 3553:3808, ack 674, win 9, options [nop,nop,TS val 270623909 ecr 2160417370], length 255
21:57:18.418149 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [.], ack 1427, win 9, options [nop,nop,TS val 270623911 ecr 2160417371], length 0
21:57:18.418175 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 4125, win 501, options [nop,nop,TS val 2160418084 ecr 270623909], length 0
21:57:18.418201 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [P.], seq 4125:4173, ack 1427, win 9, options [nop,nop,TS val 270623911 ecr 2160417371], length 48
21:57:18.418217 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 4173, win 501, options [nop,nop,TS val 2160418084 ecr 270623911], length 0
21:57:18.418301 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [P.], seq 4173:5076, ack 1427, win 9, options [nop,nop,TS val 270623912 ecr 2160417371], length 903
21:57:18.418308 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [.], ack 5076, win 501, options [nop,nop,TS val 2160418084 ecr 270623912], length 0
21:57:18.418342 IP 192.168.0.195.37356 > 13.235.147.72.443: Flags [P.], seq 1427:1458, ack 5076, win 501, options [nop,nop,TS val 2160418084 ecr 270623912], length 31
21:57:18.742720 IP 13.235.147.72.443 > 192.168.0.195.37358: Flags [P.], seq 3553:3808, ack 582, win 9, options [nop,nop,TS val 76219662 ecr 2160417647], length 255
21:57:18.742721 IP 13.235.147.72.443 > 192.168.0.195.37358: Flags [P.], seq 3808:4063, ack 582, win 9, options [nop,nop,TS val 76219662 ecr 2160417647], length 255
21:57:18.742722 IP 135.181.38.249.443 > 192.168.0.195.40834: Flags [P.], seq 69:104, ack 94, win 501, options [nop,nop,TS val 1473686206 ecr 1705147683], length 35
21:57:18.742758 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [.], ack 3808, win 501, options [nop,nop,TS val 2160418408 ecr 76219662], length 0
21:57:18.742780 IP 192.168.0.195.37358 > 13.235.147.72.443: Flags [.], ack 4063, win 501, options [nop,nop,TS val 2160418408 ecr 76219662], length 0
21:57:18.742789 IP 192.168.0.195.40834 > 135.181.38.249.443: Flags [.], ack 104, win 501, options [nop,nop,TS val 1705148062 ecr 1473686206], length 0
21:57:18.743144 IP 135.181.38.249.443 > 192.168.0.195.40834: Flags [P.], seq 104:435, ack 368, win 501, options [nop,nop,TS val 1473686220 ecr 1705147683], length 331
21:57:18.743162 IP 192.168.0.195.40834 > 135.181.38.249.443: Flags [.], ack 435, win 501, options [nop,nop,TS val 1705148063 ecr 1473686220], length 0
21:57:19.452263 IP 13.235.147.72.443 > 192.168.0.195.37356: Flags [.], ack 1458, win 9, options [nop,nop,TS val 270624098 ecr 2160418084], length 0
21:57:20.020860 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [P.], seq 1464191362:1464191401, ack 2558596083, win 501, options [nop,nop,TS val 3733393196 ecr 3698011271], length 39
21:57:20.021330 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [P.], seq 39:63, ack 1, win 501, options [nop,nop,TS val 3733393196 ecr 3698011271], length 24
21:57:20.021359 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [F.], seq 63, ack 1, win 501, options [nop,nop,TS val 3733393196 ecr 3698011271], length 0
21:57:20.164177 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [F.], seq 63, ack 1, win 501, options [nop,nop,TS val 3733393339 ecr 3698011271], length 0
21:57:20.447638 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [FP.], seq 0:63, ack 1, win 501, options [nop,nop,TS val 3733393622 ecr 3698011271], length 63
21:57:20.452696 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [.], ack 63, win 276, options [nop,nop,TS val 3698064371 ecr 3733393196], length 0
21:57:20.452698 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [.], ack 0, win 276, options [nop,nop,TS val 3698064371 ecr 3733340175,nop,nop,sack 1 {39:63}], length 0
21:57:20.452765 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [.], ack 1, win 501, options [nop,nop,TS val 3733393627 ecr 3698064371], length 0
21:57:20.452917 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [.], ack 64, win 276, options [nop,nop,TS val 3698064376 ecr 3733393196], length 0
21:57:20.452919 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [F.], seq 1, ack 64, win 276, options [nop,nop,TS val 3698064382 ecr 3733393196], length 0
21:57:20.453008 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [.], ack 2, win 501, options [nop,nop,TS val 3733393628 ecr 3698064382], length 0
21:57:20.454140 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [.], ack 64, win 276, options [nop,nop,TS val 3698064494 ecr 3733393339,nop,nop,sack 1 {63:64}], length 0
21:57:20.484047 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [F.], seq 1, ack 64, win 276, options [nop,nop,TS val 3698064650 ecr 3733393339], length 0
21:57:20.484104 IP 192.168.0.195.48578 > 172.217.170.36.443: Flags [.], ack 2, win 501, options [nop,nop,TS val 3733393659 ecr 3698064494], length 0
21:57:20.662664 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [.], ack 64, win 276, options [nop,nop,TS val 3698064774 ecr 3733393622,nop,nop,sack 1 {0:64}], length 0
21:57:20.694737 IP 172.217.170.36.443 > 192.168.0.195.48578: Flags [R], seq 2558596084, win 0, length 0
21:57:21.034206 IP 192.168.0.195.37338 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160420700 ecr 238176317], length 0
21:57:21.034213 IP 192.168.0.195.37334 > 13.235.147.72.443: Flags [F.], seq 0, ack 1, win 501, options [nop,nop,TS val 2160420700 ecr 227378373], length 0
^C
140 packets captured
140 packets received by filter
0 packets dropped by kernel
I’ve filtered by host, so here is clean results:
[chawila@devTool Desktop]$ sudo tcpdump -n dst host upwork-usw2-desktopapp.upwork.com
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on enp2s0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
22:02:17.431469 IP 192.168.0.195.35124 > 146.112.56.21.443: Flags [S], seq 172504851, win 64240, options [mss 1460,sackOK,TS val 3461976670 ecr 0,nop,wscale 7], length 0
22:02:17.632319 IP 192.168.0.195.44884 > 146.112.56.55.443: Flags [S], seq 2408742607, win 64240, options [mss 1460,sackOK,TS val 1396359423 ecr 0,nop,wscale 7], length 0
22:02:17.656133 IP 192.168.0.195.35124 > 146.112.56.21.443: Flags [.], ack 632482036, win 502, options [nop,nop,TS val 3461976895 ecr 539874453], length 0
22:02:17.669916 IP 192.168.0.195.35124 > 146.112.56.21.443: Flags [P.], seq 0:517, ack 1, win 502, options [nop,nop,TS val 3461976909 ecr 539874453], length 517
22:02:17.870830 IP 192.168.0.195.35124 > 146.112.56.21.443: Flags [.], ack 2, win 502, options [nop,nop,TS val 3461977109 ecr 539874675], length 0
22:02:17.871502 IP 192.168.0.195.35124 > 146.112.56.21.443: Flags [F.], seq 517, ack 2, win 502, options [nop,nop,TS val 3461977110 ecr 539874675], length 0
22:02:17.876893 IP 192.168.0.195.44884 > 146.112.56.55.443: Flags [R], seq 2408742608, win 0, length 0
After the first 517 bytes of data sent from you, the server initiates a connection termination for some reason.
I do not understand were u’re going with this.
i’ve just installed this OS, and i do not know much about networking
Don’t ask me. ![]()
Maybe the IP-Address that you’ve got right now has been used by someone doing nasty stuff before.
Did you try to reboot your router or reconnect (to force an IP-Address change) and then try again?
Try TOR browser or VPN or a proxy and see if things are different then…
@moson
i can log-in on upwork without any VPN, the only problem that i face is using their Desktop App.
What I meant is to try via a VPN or anything (or try going via mobile phone (tethering)) that does effectively change your IP address just to find out if it is your IP-Address that is currently blocked on their side…
First thing i would try is to restart / reconnect the router to force an address change (note down your external IP address before and after to be sure it changed).
I have a dual boot (Windows & Manjaro), both have upwork desktop client.
Window can access the desktop client without any problem.
But Manjaro cannot not.
Which prove that upwork did not block me.
And even my phone has upwork (Android) and it is connected to the same Router…
So i really don’t want to believe UpWork has blocked me. 
Edit
If Upwork wanted me out of their platform, they would closed my account. 
And i even spoke to them about this issue, they told me everything is fine on their side, the issue is on my side.
That is all really strange indeed.
And it is info that “we” didn’t have.
You where on Ubuntu, you said.
And have had … similar problems there.
One perhaps interesting thing to try and see the result of -
to me, anyway, if I where you -
would be to boot the installation medium of Manjaro
and try that curl and wget command there
and - if you still have it around
do the same with an Ubuntu or other live linux medium
just to see whether there is a difference in behaviour
between your now actual installation
and … the other, not as current, flavours of linux
Ok, good. At least you can sort that one out now.
Back to the issue:
What I find weird is the addresses that are resolved on your end for upwork-usw2-desktopapp.upwork.com
On my end this is:
upwork-usw2-desktopapp.upwork.com. 300 IN A 104.18.89.237
upwork-usw2-desktopapp.upwork.com. 300 IN A 104.18.90.237
On your end it seems to be “146.112.252.240”.
And that one seems to belong to “OPENDNS”:
role: OPENDNS NETENG TEAM
address: OpenDNS
address: 675 West Hastings Street, Suite 500
address: Vancouver BC V6B 1N2
address: Canada
Something is odd.
Please post dig upwork-usw2-desktopapp.upwork.com
@moson Sorry for the late response.
[chawila@devTool ~]$ dig upwork-usw2-desktopapp.upwork.com
; <<>> DiG 9.16.13 <<>> upwork-usw2-desktopapp.upwork.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 32754
;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;upwork-usw2-desktopapp.upwork.com. IN A
;; ANSWER SECTION:
upwork-usw2-desktopapp.upwork.com. 4 IN A 146.112.56.190
upwork-usw2-desktopapp.upwork.com. 4 IN A 146.112.56.55
upwork-usw2-desktopapp.upwork.com. 4 IN A 146.112.56.139
upwork-usw2-desktopapp.upwork.com. 4 IN A 146.112.56.187
upwork-usw2-desktopapp.upwork.com. 4 IN A 146.112.56.182
upwork-usw2-desktopapp.upwork.com. 4 IN A 146.112.56.21
;; Query time: 256 msec
;; SERVER: 192.168.0.1#53(192.168.0.1)
;; WHEN: Wed Apr 28 22:43:08 SAST 2021
;; MSG SIZE rcvd: 158