I’m trying to create an encrypted partition for my /home which I will later automount.
Problem is, cryptsetup is unable to deal with LUKS2, for some reason.
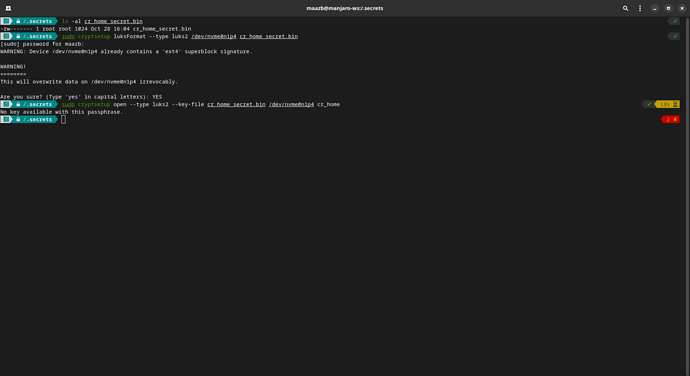
- Created a key file
$ sudo dd if=/dev/urandom of=cr_home_secret.bin bs=1024 count=1
1+0 records in
1+0 records out
1024 bytes (1.0 kB, 1.0 KiB) copied, 7.9413e-05 s, 12.9 MB/s
- luksFormat existing
ext4partition
$ sudo cryptsetup --type luks2 luksFormat /dev/nvme0n1p4 cr_home_secret.bin
WARNING: Device /dev/nvme0n1p4 already contains a 'ext4' superblock signature.
WARNING!
========
This will overwrite data on /dev/nvme0n1p4 irrevocably.
Are you sure? (Type 'yes' in capital letters): YES
- Open the luks container to fromat the partition
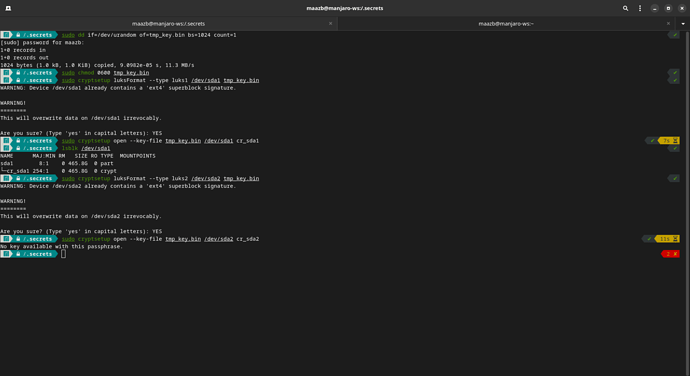
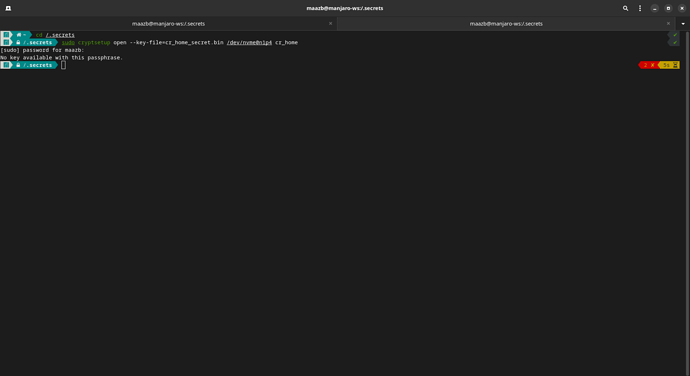
$ sudo cryptsetup --key-file=cr_home_secret.bin open /dev/nvme0n1p4 cr_home
No key available with this passphrase.
I’ve done this so many times before but this is just weird!
Any ideas as to what I might be going on?
luksDump
$ sudo cryptsetup luksDump /dev/nvme0n1p4
LUKS header information
Version: 2
Epoch: 3
Metadata area: 16384 [bytes]
Keyslots area: 16744448 [bytes]
UUID: 08911182-9a4c-41b5-93ae-b06b273efd06
Label: (no label)
Subsystem: (no subsystem)
Flags: (no flags)
Data segments:
0: crypt
offset: 16777216 [bytes]
length: (whole device)
cipher: aes-xts-plain64
sector: 512 [bytes]
Keyslots:
0: luks2
Key: 512 bits
Priority: normal
Cipher: aes-xts-plain64
Cipher key: 512 bits
PBKDF: argon2id
Time cost: 10
Memory: 1048576
Threads: 4
Salt: 1e 72 e5 70 7e 5d 28 82 53 57 20 15 53 04 ea 55
4f e9 90 5b 89 81 0b 38 35 b9 4e 0f 23 70 21 9f
AF stripes: 4000
AF hash: sha256
Area offset:32768 [bytes]
Area length:258048 [bytes]
Digest ID: 0
Tokens:
Digests:
0: pbkdf2
Hash: sha256
Iterations: 301661
Salt: 64 88 d0 58 5d 3f 68 61 d9 df 07 f8 13 6f d8 33
a7 f8 b2 e6 3b cf 26 8f a5 56 e8 04 00 b4 b9 69
Digest: d2 c0 83 bb 16 12 d6 cc 3f a9 e2 eb 09 c0 ec 8f
b1 59 3e ca c8 12 f0 e7 35 a4 1c cb 0a 22 1f fe
hexdump
$ sudo dd if=/dev/nvme0n1p4 bs=32k count=1 status=none | hexdump -C
00000000 4c 55 4b 53 ba be 00 02 00 00 00 00 00 00 40 00 |LUKS..........@.|
00000010 00 00 00 00 00 00 00 03 00 00 00 00 00 00 00 00 |................|
00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00000040 00 00 00 00 00 00 00 00 73 68 61 32 35 36 00 00 |........sha256..|
00000050 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000060 00 00 00 00 00 00 00 00 4d 2e 66 45 4f 52 9a 98 |........M.fEOR..|
00000070 90 50 73 d0 8b d6 5c 30 3f 75 52 a0 bb eb 8a 41 |.Ps...\0?uR....A|
00000080 f7 da b7 f4 9d 2e e6 c2 5f ef 59 ed 3b f9 93 49 |........_.Y.;..I|
00000090 2a ef 93 d0 50 f1 2f 86 4e da 4f 91 bd 43 58 a0 |*...P./.N.O..CX.|
000000a0 86 6e db 57 49 25 61 10 65 37 63 36 64 37 38 37 |.n.WI%a.e7c6d787|
000000b0 2d 61 32 37 31 2d 34 38 62 35 2d 62 61 61 61 2d |-a271-48b5-baaa-|
000000c0 36 32 65 34 32 36 33 33 66 37 39 65 00 00 00 00 |62e42633f79e....|
000000d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
000001c0 5e ab 0a a2 d0 a4 f9 ad d5 3e 99 17 2d 68 1b 9d |^........>..-h..|
000001d0 ac ce 40 7d b9 3d de 5a c2 ab 7d 4f ed af 75 22 |..@}.=.Z..}O..u"|
000001e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00001000 7b 22 6b 65 79 73 6c 6f 74 73 22 3a 7b 22 30 22 |{"keyslots":{"0"|
00001010 3a 7b 22 74 79 70 65 22 3a 22 6c 75 6b 73 32 22 |:{"type":"luks2"|
00001020 2c 22 6b 65 79 5f 73 69 7a 65 22 3a 36 34 2c 22 |,"key_size":64,"|
00001030 61 66 22 3a 7b 22 74 79 70 65 22 3a 22 6c 75 6b |af":{"type":"luk|
00001040 73 31 22 2c 22 73 74 72 69 70 65 73 22 3a 34 30 |s1","stripes":40|
00001050 30 30 2c 22 68 61 73 68 22 3a 22 73 68 61 32 35 |00,"hash":"sha25|
00001060 36 22 7d 2c 22 61 72 65 61 22 3a 7b 22 74 79 70 |6"},"area":{"typ|
00001070 65 22 3a 22 72 61 77 22 2c 22 6f 66 66 73 65 74 |e":"raw","offset|
00001080 22 3a 22 33 32 37 36 38 22 2c 22 73 69 7a 65 22 |":"32768","size"|
00001090 3a 22 32 35 38 30 34 38 22 2c 22 65 6e 63 72 79 |:"258048","encry|
000010a0 70 74 69 6f 6e 22 3a 22 61 65 73 2d 78 74 73 2d |ption":"aes-xts-|
000010b0 70 6c 61 69 6e 36 34 22 2c 22 6b 65 79 5f 73 69 |plain64","key_si|
000010c0 7a 65 22 3a 36 34 7d 2c 22 6b 64 66 22 3a 7b 22 |ze":64},"kdf":{"|
000010d0 74 79 70 65 22 3a 22 61 72 67 6f 6e 32 69 64 22 |type":"argon2id"|
000010e0 2c 22 74 69 6d 65 22 3a 31 30 2c 22 6d 65 6d 6f |,"time":10,"memo|
000010f0 72 79 22 3a 31 30 34 38 35 37 36 2c 22 63 70 75 |ry":1048576,"cpu|
00001100 73 22 3a 34 2c 22 73 61 6c 74 22 3a 22 6b 70 49 |s":4,"salt":"kpI|
00001110 56 5a 56 2f 6c 4b 61 31 2f 2f 50 79 7a 6c 6a 78 |VZV/lKa1//Pyzljx|
00001120 77 64 30 2f 36 6b 6b 64 63 69 69 44 46 32 35 31 |wd0/6kkdciiDF251|
00001130 4c 30 69 45 49 34 47 67 3d 22 7d 7d 7d 2c 22 74 |L0iEI4Gg="}}},"t|
00001140 6f 6b 65 6e 73 22 3a 7b 7d 2c 22 73 65 67 6d 65 |okens":{},"segme|
00001150 6e 74 73 22 3a 7b 22 30 22 3a 7b 22 74 79 70 65 |nts":{"0":{"type|
00001160 22 3a 22 63 72 79 70 74 22 2c 22 6f 66 66 73 65 |":"crypt","offse|
00001170 74 22 3a 22 31 36 37 37 37 32 31 36 22 2c 22 73 |t":"16777216","s|
00001180 69 7a 65 22 3a 22 64 79 6e 61 6d 69 63 22 2c 22 |ize":"dynamic","|
00001190 69 76 5f 74 77 65 61 6b 22 3a 22 30 22 2c 22 65 |iv_tweak":"0","e|
000011a0 6e 63 72 79 70 74 69 6f 6e 22 3a 22 61 65 73 2d |ncryption":"aes-|
000011b0 78 74 73 2d 70 6c 61 69 6e 36 34 22 2c 22 73 65 |xts-plain64","se|
000011c0 63 74 6f 72 5f 73 69 7a 65 22 3a 35 31 32 7d 7d |ctor_size":512}}|
000011d0 2c 22 64 69 67 65 73 74 73 22 3a 7b 22 30 22 3a |,"digests":{"0":|
000011e0 7b 22 74 79 70 65 22 3a 22 70 62 6b 64 66 32 22 |{"type":"pbkdf2"|
000011f0 2c 22 6b 65 79 73 6c 6f 74 73 22 3a 5b 22 30 22 |,"keyslots":["0"|
00001200 5d 2c 22 73 65 67 6d 65 6e 74 73 22 3a 5b 22 30 |],"segments":["0|
00001210 22 5d 2c 22 68 61 73 68 22 3a 22 73 68 61 32 35 |"],"hash":"sha25|
00001220 36 22 2c 22 69 74 65 72 61 74 69 6f 6e 73 22 3a |6","iterations":|
00001230 32 39 34 32 31 33 2c 22 73 61 6c 74 22 3a 22 5a |294213,"salt":"Z|
00001240 38 2b 75 4c 4d 4e 6c 4c 71 6e 63 6a 37 54 75 71 |8+uLMNlLqncj7Tuq|
00001250 31 58 46 46 2f 6e 6a 44 6b 38 61 2f 76 76 79 76 |1XFF/njDk8a/vvyv|
00001260 4e 61 69 6f 77 6a 64 74 2b 59 3d 22 2c 22 64 69 |Naiowjdt+Y=","di|
00001270 67 65 73 74 22 3a 22 47 31 66 4e 45 43 36 51 4b |gest":"G1fNEC6QK|
00001280 34 46 43 37 68 72 38 79 44 66 34 61 45 42 33 78 |4FC7hr8yDf4aEB3x|
00001290 75 4a 55 2f 6e 64 32 74 70 66 42 4c 45 73 46 72 |uJU/nd2tpfBLEsFr|
000012a0 63 63 3d 22 7d 7d 2c 22 63 6f 6e 66 69 67 22 3a |cc="}},"config":|
000012b0 7b 22 6a 73 6f 6e 5f 73 69 7a 65 22 3a 22 31 32 |{"json_size":"12|
000012c0 32 38 38 22 2c 22 6b 65 79 73 6c 6f 74 73 5f 73 |288","keyslots_s|
000012d0 69 7a 65 22 3a 22 31 36 37 34 34 34 34 38 22 7d |ize":"16744448"}|
000012e0 7d 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |}...............|
000012f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00004000 53 4b 55 4c ba be 00 02 00 00 00 00 00 00 40 00 |SKUL..........@.|
00004010 00 00 00 00 00 00 00 03 00 00 00 00 00 00 00 00 |................|
00004020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00004040 00 00 00 00 00 00 00 00 73 68 61 32 35 36 00 00 |........sha256..|
00004050 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00004060 00 00 00 00 00 00 00 00 71 f6 1d 7c c9 d7 34 b7 |........q..|..4.|
00004070 e6 6c e9 48 a6 81 0f 2d a5 09 2a f2 5a 9b 2c 64 |.l.H...-..*.Z.,d|
00004080 80 cc 84 b8 77 26 6f e1 de 76 f2 4e b0 8a 55 39 |....w&o..v.N..U9|
00004090 ac 89 9f 00 00 82 68 96 3f 7e ef b0 a2 98 8c 77 |......h.?~.....w|
000040a0 e6 70 bf b6 93 a9 c5 2d 65 37 63 36 64 37 38 37 |.p.....-e7c6d787|
000040b0 2d 61 32 37 31 2d 34 38 62 35 2d 62 61 61 61 2d |-a271-48b5-baaa-|
000040c0 36 32 65 34 32 36 33 33 66 37 39 65 00 00 00 00 |62e42633f79e....|
000040d0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00004100 00 00 00 00 00 00 40 00 00 00 00 00 00 00 00 00 |......@.........|
00004110 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
000041c0 d2 c7 75 0b 4b e0 e4 d1 3e 48 ff 53 eb 1b 1e b7 |..u.K...>H.S....|
000041d0 c4 a3 d3 cf 51 86 d7 c3 38 96 5a df 6d 89 18 cb |....Q...8.Z.m...|
000041e0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00005000 7b 22 6b 65 79 73 6c 6f 74 73 22 3a 7b 22 30 22 |{"keyslots":{"0"|
00005010 3a 7b 22 74 79 70 65 22 3a 22 6c 75 6b 73 32 22 |:{"type":"luks2"|
00005020 2c 22 6b 65 79 5f 73 69 7a 65 22 3a 36 34 2c 22 |,"key_size":64,"|
00005030 61 66 22 3a 7b 22 74 79 70 65 22 3a 22 6c 75 6b |af":{"type":"luk|
00005040 73 31 22 2c 22 73 74 72 69 70 65 73 22 3a 34 30 |s1","stripes":40|
00005050 30 30 2c 22 68 61 73 68 22 3a 22 73 68 61 32 35 |00,"hash":"sha25|
00005060 36 22 7d 2c 22 61 72 65 61 22 3a 7b 22 74 79 70 |6"},"area":{"typ|
00005070 65 22 3a 22 72 61 77 22 2c 22 6f 66 66 73 65 74 |e":"raw","offset|
00005080 22 3a 22 33 32 37 36 38 22 2c 22 73 69 7a 65 22 |":"32768","size"|
00005090 3a 22 32 35 38 30 34 38 22 2c 22 65 6e 63 72 79 |:"258048","encry|
000050a0 70 74 69 6f 6e 22 3a 22 61 65 73 2d 78 74 73 2d |ption":"aes-xts-|
000050b0 70 6c 61 69 6e 36 34 22 2c 22 6b 65 79 5f 73 69 |plain64","key_si|
000050c0 7a 65 22 3a 36 34 7d 2c 22 6b 64 66 22 3a 7b 22 |ze":64},"kdf":{"|
000050d0 74 79 70 65 22 3a 22 61 72 67 6f 6e 32 69 64 22 |type":"argon2id"|
000050e0 2c 22 74 69 6d 65 22 3a 31 30 2c 22 6d 65 6d 6f |,"time":10,"memo|
000050f0 72 79 22 3a 31 30 34 38 35 37 36 2c 22 63 70 75 |ry":1048576,"cpu|
00005100 73 22 3a 34 2c 22 73 61 6c 74 22 3a 22 6b 70 49 |s":4,"salt":"kpI|
00005110 56 5a 56 2f 6c 4b 61 31 2f 2f 50 79 7a 6c 6a 78 |VZV/lKa1//Pyzljx|
00005120 77 64 30 2f 36 6b 6b 64 63 69 69 44 46 32 35 31 |wd0/6kkdciiDF251|
00005130 4c 30 69 45 49 34 47 67 3d 22 7d 7d 7d 2c 22 74 |L0iEI4Gg="}}},"t|
00005140 6f 6b 65 6e 73 22 3a 7b 7d 2c 22 73 65 67 6d 65 |okens":{},"segme|
00005150 6e 74 73 22 3a 7b 22 30 22 3a 7b 22 74 79 70 65 |nts":{"0":{"type|
00005160 22 3a 22 63 72 79 70 74 22 2c 22 6f 66 66 73 65 |":"crypt","offse|
00005170 74 22 3a 22 31 36 37 37 37 32 31 36 22 2c 22 73 |t":"16777216","s|
00005180 69 7a 65 22 3a 22 64 79 6e 61 6d 69 63 22 2c 22 |ize":"dynamic","|
00005190 69 76 5f 74 77 65 61 6b 22 3a 22 30 22 2c 22 65 |iv_tweak":"0","e|
000051a0 6e 63 72 79 70 74 69 6f 6e 22 3a 22 61 65 73 2d |ncryption":"aes-|
000051b0 78 74 73 2d 70 6c 61 69 6e 36 34 22 2c 22 73 65 |xts-plain64","se|
000051c0 63 74 6f 72 5f 73 69 7a 65 22 3a 35 31 32 7d 7d |ctor_size":512}}|
000051d0 2c 22 64 69 67 65 73 74 73 22 3a 7b 22 30 22 3a |,"digests":{"0":|
000051e0 7b 22 74 79 70 65 22 3a 22 70 62 6b 64 66 32 22 |{"type":"pbkdf2"|
000051f0 2c 22 6b 65 79 73 6c 6f 74 73 22 3a 5b 22 30 22 |,"keyslots":["0"|
00005200 5d 2c 22 73 65 67 6d 65 6e 74 73 22 3a 5b 22 30 |],"segments":["0|
00005210 22 5d 2c 22 68 61 73 68 22 3a 22 73 68 61 32 35 |"],"hash":"sha25|
00005220 36 22 2c 22 69 74 65 72 61 74 69 6f 6e 73 22 3a |6","iterations":|
00005230 32 39 34 32 31 33 2c 22 73 61 6c 74 22 3a 22 5a |294213,"salt":"Z|
00005240 38 2b 75 4c 4d 4e 6c 4c 71 6e 63 6a 37 54 75 71 |8+uLMNlLqncj7Tuq|
00005250 31 58 46 46 2f 6e 6a 44 6b 38 61 2f 76 76 79 76 |1XFF/njDk8a/vvyv|
00005260 4e 61 69 6f 77 6a 64 74 2b 59 3d 22 2c 22 64 69 |Naiowjdt+Y=","di|
00005270 67 65 73 74 22 3a 22 47 31 66 4e 45 43 36 51 4b |gest":"G1fNEC6QK|
00005280 34 46 43 37 68 72 38 79 44 66 34 61 45 42 33 78 |4FC7hr8yDf4aEB3x|
00005290 75 4a 55 2f 6e 64 32 74 70 66 42 4c 45 73 46 72 |uJU/nd2tpfBLEsFr|
000052a0 63 63 3d 22 7d 7d 2c 22 63 6f 6e 66 69 67 22 3a |cc="}},"config":|
000052b0 7b 22 6a 73 6f 6e 5f 73 69 7a 65 22 3a 22 31 32 |{"json_size":"12|
000052c0 32 38 38 22 2c 22 6b 65 79 73 6c 6f 74 73 5f 73 |288","keyslots_s|
000052d0 69 7a 65 22 3a 22 31 36 37 34 34 34 34 38 22 7d |ize":"16744448"}|
000052e0 7d 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |}...............|
000052f0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
*
00008000
inxi
$ sudo inxi -Fazy
System:
Kernel: 5.15.74-3-MANJARO arch: x86_64 bits: 64 compiler: gcc v: 12.2.0
parameters: BOOT_IMAGE=/vmlinuz-5.15-x86_64
root=UUID=f0841d97-6be1-412d-bbe8-c32be5ed279c rw rootflags=subvol=@ quiet
cryptdevice=UUID=fb020f9f-eb78-4372-8c21-aee7953b1b95:cr_root
root=/dev/mapper/cr_root udev.log_priority=3
Desktop: GNOME v: 42.5 tk: GTK v: 3.24.34 wm: gnome-shell dm: GDM v: 42.0
Distro: Manjaro Linux base: Arch Linux
Machine:
Type: Desktop Mobo: ASUSTeK model: TUF GAMING X570-PLUS (WI-FI) v: Rev X.0x
serial: <filter> UEFI: American Megatrends v: 3603 date: 03/20/2021
CPU:
Info: model: AMD Ryzen 7 3700X socket: AM4 bits: 64 type: MT MCP arch: Zen 2
gen: 3 level: v3 note: check built: 2020-22 process: TSMC n7 (7nm)
family: 0x17 (23) model-id: 0x71 (113) stepping: 0 microcode: 0x8701021
Topology: cpus: 1x cores: 8 tpc: 2 threads: 16 smt: enabled cache:
L1: 512 KiB desc: d-8x32 KiB; i-8x32 KiB L2: 4 MiB desc: 8x512 KiB
L3: 32 MiB desc: 2x16 MiB
Speed (MHz): avg: 2375 high: 3600 min/max: 2200/4426 boost: enabled
base/boost: 3600/4400 scaling: driver: acpi-cpufreq governor: schedutil
volts: 1.1 V ext-clock: 100 MHz cores: 1: 2200 2: 2200 3: 2200 4: 2200
5: 2200 6: 2200 7: 2200 8: 2200 9: 3600 10: 2200 11: 3600 12: 2200
13: 2200 14: 2200 15: 2200 16: 2200 bogomips: 115242
Flags: avx avx2 ht lm nx pae sse sse2 sse3 sse4_1 sse4_2 sse4a ssse3 svm
Vulnerabilities:
Type: itlb_multihit status: Not affected
Type: l1tf status: Not affected
Type: mds status: Not affected
Type: meltdown status: Not affected
Type: mmio_stale_data status: Not affected
Type: retbleed mitigation: untrained return thunk; SMT enabled with STIBP
protection
Type: spec_store_bypass mitigation: Speculative Store Bypass disabled via
prctl and seccomp
Type: spectre_v1 mitigation: usercopy/swapgs barriers and __user pointer
sanitization
Type: spectre_v2 mitigation: Retpolines, IBPB: conditional, STIBP:
always-on, RSB filling, PBRSB-eIBRS: Not affected
Type: srbds status: Not affected
Type: tsx_async_abort status: Not affected
Graphics:
Device-1: NVIDIA TU104GL [Quadro RTX 4000] driver: nvidia v: 470.141.03
alternate: nouveau,nvidia_drm non-free: 515.xx+ status: current (as of
2022-10) arch: Turing code: TUxxx process: TSMC 12nm built: 2018-22 pcie:
gen: 1 speed: 2.5 GT/s lanes: 16 link-max: gen: 3 speed: 8 GT/s
bus-ID: 0a:00.0 chip-ID: 10de:1eb1 class-ID: 0300
Display: server: X.org v: 1.21.1.4 with: Xwayland v: 22.1.3
compositor: gnome-shell driver: X: loaded: nvidia gpu: nvidia display-ID: :1
screens: 1
Screen-1: 0 s-res: 1920x1080 s-size: <missing: xdpyinfo>
Monitor-1: DP-3 res: 1920x1080 hz: 60 dpi: 102
size: 476x268mm (18.74x10.55") diag: 546mm (21.51") modes: N/A
OpenGL: renderer: Quadro RTX 4000/PCIe/SSE2 v: 4.6.0 NVIDIA 470.141.03
direct render: Yes
Audio:
Device-1: NVIDIA TU104 HD Audio driver: snd_hda_intel v: kernel pcie: gen: 3
speed: 8 GT/s lanes: 16 bus-ID: 0a:00.1 chip-ID: 10de:10f8 class-ID: 0403
Device-2: AMD Starship/Matisse HD Audio vendor: ASUSTeK
driver: snd_hda_intel v: kernel pcie: gen: 4 speed: 16 GT/s lanes: 16
bus-ID: 0c:00.4 chip-ID: 1022:1487 class-ID: 0403
Sound API: ALSA v: k5.15.74-3-MANJARO running: yes
Sound Server-1: JACK v: 1.9.21 running: no
Sound Server-2: PulseAudio v: 16.1 running: yes
Sound Server-3: PipeWire v: 0.3.58 running: no
Network:
Device-1: Intel Wireless-AC 9260 driver: iwlwifi v: kernel pcie: gen: 2
speed: 5 GT/s lanes: 1 bus-ID: 05:00.0 chip-ID: 8086:2526 class-ID: 0280
IF: wlp5s0 state: up mac: <filter>
Device-2: Realtek RTL8111/8168/8411 PCI Express Gigabit Ethernet
vendor: ASUSTeK driver: r8169 v: kernel pcie: gen: 1 speed: 2.5 GT/s
lanes: 1 port: f000 bus-ID: 06:00.0 chip-ID: 10ec:8168 class-ID: 0200
IF: enp6s0 state: down mac: <filter>
Bluetooth:
Device-1: Intel Wireless-AC 9260 Bluetooth Adapter type: USB driver: btusb
v: 0.8 bus-ID: 3-5:3 chip-ID: 8087:0025 class-ID: e001
Report: rfkill ID: hci0 rfk-id: 0 state: up address: see --recommends
Drives:
Local Storage: total: 3.24 TiB used: 8.45 GiB (0.3%)
SMART Message: Required tool smartctl not installed. Check --recommends
ID-1: /dev/nvme0n1 maj-min: 259:0 vendor: KIOXIA model: EXCERIA SSD
size: 931.51 GiB block-size: physical: 512 B logical: 512 B speed: 31.6 Gb/s
lanes: 4 type: SSD serial: <filter> rev: ECFA12.9 temp: 43.9 C scheme: GPT
ID-2: /dev/nvme1n1 maj-min: 259:4 vendor: Silicon Power model: SPCC M.2
PCIe SSD size: 476.94 GiB block-size: physical: 512 B logical: 512 B
speed: 31.6 Gb/s lanes: 4 type: SSD serial: <filter> rev: EDFM20.0
temp: 23.9 C scheme: GPT
ID-3: /dev/sda maj-min: 8:0 vendor: Crucial model: CT1000MX500SSD1
size: 931.51 GiB block-size: physical: 4096 B logical: 512 B speed: 6.0 Gb/s
type: SSD serial: <filter> rev: 023 scheme: GPT
ID-4: /dev/sdb maj-min: 8:16 vendor: Crucial model: CT1000MX500SSD1
size: 931.51 GiB block-size: physical: 4096 B logical: 512 B speed: 6.0 Gb/s
type: SSD serial: <filter> rev: 043 scheme: GPT
ID-5: /dev/sdc maj-min: 8:32 type: USB vendor: HP model: v301w
size: 14.47 GiB block-size: physical: 512 B logical: 512 B type: N/A
serial: <filter> rev: PMAP scheme: GPT
ID-6: /dev/sdd maj-min: 8:48 type: USB vendor: SanDisk model: Ultra USB
3.0 size: 28.64 GiB block-size: physical: 512 B logical: 512 B type: N/A
serial: <filter> rev: 1.00 scheme: MBR
Partition:
ID-1: / raw-size: 59.6 GiB size: 59.6 GiB (100.00%) used: 8.38 GiB (14.1%)
fs: btrfs block-size: 4096 B dev: /dev/dm-0 maj-min: 254:0 mapped: cr_root
ID-2: /boot raw-size: 732 MiB size: 703.8 MiB (96.14%) used: 70.3 MiB
(10.0%) fs: ext4 block-size: 4096 B dev: /dev/nvme0n1p2 maj-min: 259:2
ID-3: /boot/efi raw-size: 244 MiB size: 240.2 MiB (98.46%) used: 298 KiB
(0.1%) fs: vfat block-size: 512 B dev: /dev/nvme0n1p1 maj-min: 259:1
ID-4: /home raw-size: 59.6 GiB size: 59.6 GiB (100.00%) used: 8.38 GiB
(14.1%) fs: btrfs block-size: 4096 B dev: /dev/dm-0 maj-min: 254:0
mapped: cr_root
ID-5: /var/log raw-size: 59.6 GiB size: 59.6 GiB (100.00%) used: 8.38 GiB
(14.1%) fs: btrfs block-size: 4096 B dev: /dev/dm-0 maj-min: 254:0
mapped: cr_root
Swap:
Alert: No swap data was found.
Sensors:
System Temperatures: cpu: 44.0 C mobo: N/A gpu: nvidia temp: 48 C
Fan Speeds (RPM): N/A gpu: nvidia fan: 30%
Info:
Processes: 394 Uptime: 27m wakeups: 1 Memory: 31.26 GiB used: 2.24 GiB
(7.2%) Init: systemd v: 251 default: graphical tool: systemctl Compilers:
gcc: 12.2.0 clang: 14.0.6 Packages: pm: pacman pkgs: 846 libs: 254
tools: gnome-software,pamac Shell: Zsh (sudo) v: 5.9 default: Bash v: 5.1.16
running-in: gnome-terminal inxi: 3.3.22