Hi,
First of all, I’m sorry, I’m a KDE Neon user, not a Manjaro Linux user. A lot of Google search results pointed me to this forum. I read and learned a lot here the last 3 days! I’m 99% sure my problem is applicable to Manjaro Linux or any Linux distribution. I hope somebody can help me.
I’m sorry again, but seems I cannot have permission. I try to explain the best I can.
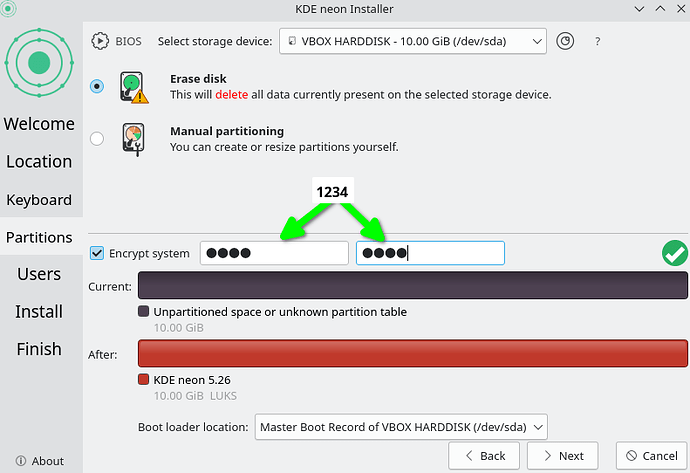
After a fresh installation of KDE neon with the default installer (calamares), with a full disk encryption I made a mistake: I removed the slot of crypto_keyfile.bin in luks.
Partition setup on calamares:
After install, the system ask me for the passphrase at boot:
![]()
All works well:

I can boot and log in.
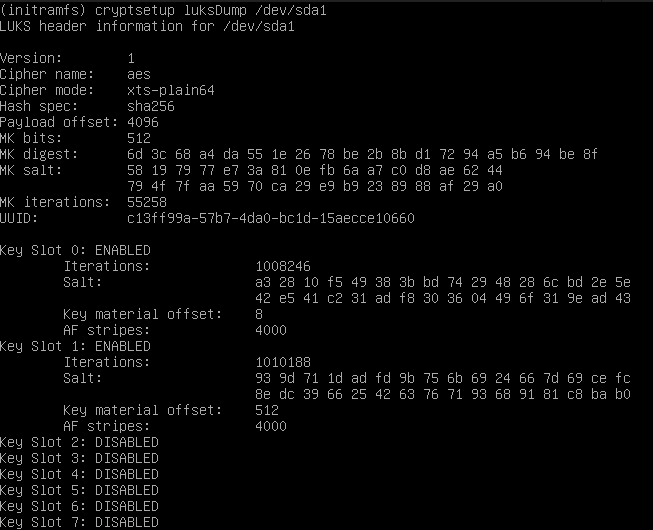
Here the initial dump of my disk at this point:
# dump after fresh install:
# cryptsetup luksDump /dev/sda1
LUKS header information for /dev/sda1
Version: 1
Cipher name: aes
Cipher mode: xts-plain64
Hash spec: sha256
Payload offset: 4096
MK bits: 512
MK digest: 6d 3c 68 a4 da 55 1e 26 78 be 2b 8b d1 72 94 a5 b6 94 be 8f
MK salt: 58 19 79 77 e7 3a 81 0e fb 6a a7 c0 d8 ae 62 44
79 4f 7f aa 59 70 ca 29 e9 b9 23 89 88 af 29 a0
MK iterations: 55258
UUID: c13ff99a-57b7-4da0-bc1d-15aecce10660
Key Slot 0: ENABLED
Iterations: 1008246
Salt: a3 28 10 f5 49 38 3b bd 74 29 48 28 6c bd 2e 5e
42 e5 41 c2 31 ad f8 30 36 04 49 6f 31 9e ad 43
Key material offset: 8
AF stripes: 4000
Key Slot 1: ENABLED
Iterations: 881156
Salt: 3b d3 2b a0 c4 93 75 4e fd 54 ca f8 12 23 15 3f
cf ce 99 1f a8 1e ab 6c d8 81 86 33 70 51 16 9c
Key material offset: 512
AF stripes: 4000
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
some relavant info:
# cat /etc/crypttab
# /etc/crypttab: mappings for encrypted partitions.
# <name> <device> <password> <options>
luks-c13ff99a-57b7-4da0-bc1d-15aecce10660 UUID=c13ff99a-57b7-4da0-bc1d-15aecce10660 /crypto_keyfile.bin luks,discard
# cat /etc/cryptsetup-initramfs/conf-hook
KEYFILE_PATTERN=/crypto_keyfile.bin
# grub.cfg
menuentry 'Neon GNU/Linux' --class neon --class gnu-linux --class gnu --class os $menuentry_id_option 'gnulinux-simple-db38bf32-cd67-433b-8098-0720751466dd' {
recordfail
load_video
gfxmode $linux_gfx_mode
insmod gzio
if [ x$grub_platform = xxen ]; then insmod xzio; insmod lzopio; fi
insmod part_msdos
insmod cryptodisk
insmod luks
insmod gcry_rijndael
insmod gcry_rijndael
insmod gcry_sha256
insmod ext2
cryptomount -u c13ff99a57b74da0bc1d15aecce10660
set root='cryptouuid/c13ff99a57b74da0bc1d15aecce10660'
if [ x$feature_platform_search_hint = xy ]; then
search --no-floppy --fs-uuid --set=root --hint='cryptouuid/c13ff99a57b74da0bc1d15aecce10660' db38bf32-cd67-433b-8098-0720751466dd
else
search --no-floppy --fs-uuid --set=root db38bf32-cd67-433b-8098-0720751466dd
fi
linux /boot/vmlinuz-5.15.0-58-generic root=UUID=db38bf32-cd67-433b-8098-0720751466dd ro quiet splash $vt_handoff
initrd /boot/initrd.img-5.15.0-58-generic
}
and now, my mistake: I tried to change the key of slot 1 instead of slot 0 (I want to change iter-time).
# cryptsetup luksChangeKey /dev/sda1 -S 1 -i 30
Enter passphrase to be changed:
No key available with this passphrase.
# cryptsetup luksKillSlot /dev/sda1 1
Enter any remaining passphrase:
# cryptsetup luksAddKey /dev/sda1 -S 1 -i 30
Enter any existing passphrase:
Enter new passphrase for key slot: # nothing entered, just enter
Verify passphrase: # nothing entered, just enter
dumps during last steps …
# dump after kill slot 1
# cryptsetup luksDump /dev/sda1
LUKS header information for /dev/sda1
Version: 1
Cipher name: aes
Cipher mode: xts-plain64
Hash spec: sha256
Payload offset: 4096
MK bits: 512
MK digest: 6d 3c 68 a4 da 55 1e 26 78 be 2b 8b d1 72 94 a5 b6 94 be 8f
MK salt: 58 19 79 77 e7 3a 81 0e fb 6a a7 c0 d8 ae 62 44
79 4f 7f aa 59 70 ca 29 e9 b9 23 89 88 af 29 a0
MK iterations: 55258
UUID: c13ff99a-57b7-4da0-bc1d-15aecce10660
Key Slot 0: ENABLED
Iterations: 1008246
Salt: a3 28 10 f5 49 38 3b bd 74 29 48 28 6c bd 2e 5e
42 e5 41 c2 31 ad f8 30 36 04 49 6f 31 9e ad 43
Key material offset: 8
AF stripes: 4000
Key Slot 1: DISABLED
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
# dump after add key
# cryptsetup luksDump /dev/sda1
LUKS header information for /dev/sda1
Version: 1
Cipher name: aes
Cipher mode: xts-plain64
Hash spec: sha256
Payload offset: 4096
MK bits: 512
MK digest: 6d 3c 68 a4 da 55 1e 26 78 be 2b 8b d1 72 94 a5 b6 94 be 8f
MK salt: 58 19 79 77 e7 3a 81 0e fb 6a a7 c0 d8 ae 62 44
79 4f 7f aa 59 70 ca 29 e9 b9 23 89 88 af 29 a0
MK iterations: 55258
UUID: c13ff99a-57b7-4da0-bc1d-15aecce10660
Key Slot 0: ENABLED
Iterations: 1008246
Salt: a3 28 10 f5 49 38 3b bd 74 29 48 28 6c bd 2e 5e
42 e5 41 c2 31 ad f8 30 36 04 49 6f 31 9e ad 43
Key material offset: 8
AF stripes: 4000
Key Slot 1: ENABLED
Iterations: 16115
Salt: 98 d6 c6 d2 c0 59 41 6b 64 cf d8 c4 d6 93 ef 85
f5 97 f7 29 f2 4f f7 03 c0 7c 16 d9 a5 54 27 99
Key material offset: 512
AF stripes: 4000
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
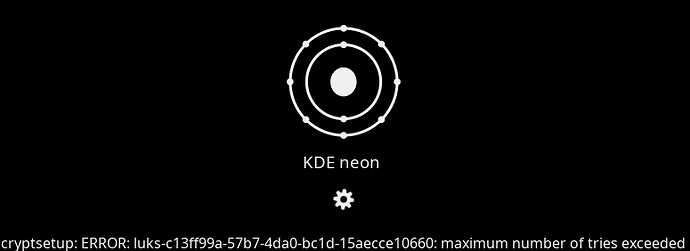
After reboot, I can see this error:
Now I’m on busybox and I try to restore in this way:
cryptsetup luksOpen /dev/sda1 try1
mount /dev/mapper/try1 /try1
cryptsetup luksChangeKey /dev/sda1 --key-slot 1 /try/crypto_file.bin
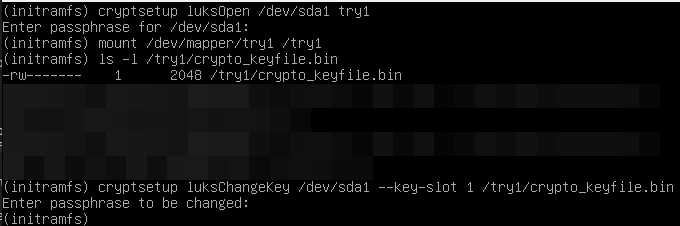
A new luksDump:
After reboot, the system not boots (cannot edit entries, boot, nothing):
What I’m missing? Where I’m misundertood? Where is my error.
Thank’s in adavance!