Great job! Did you also check the contents of the lists that you so GREATLY found (I also found them, that is why I asked) or you are more interested in acting like an ass??
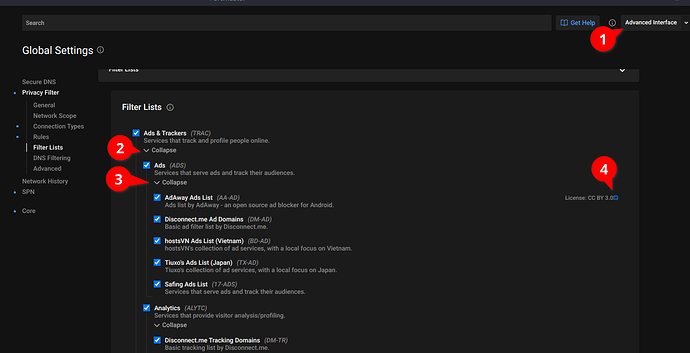
Lets chek the ads-list:
# Copyright by Intel-Data Authors
# Managed by Safing at https://github.com/safing/intel-data
# License: CC-BY-SA-4.0
analyticsnew.overwolf.com # Overwolf ads & tracking
tracking.overwolf.com # Overwolf ads & tracking
Ok…?? Seems great!
What about the fraud list??
# Copyright by Intel-Data Authors
# Managed by Safing at https://github.com/safing/intel-data
# License: CC-BY-SA-4.0
marketmetrics.digital #1 - Target: Github SSH Keys for Handshake Airdrop
Maybe I’m just unlucky, what about the malware.txt
# Copyright by Intel-Data Authors
# Managed by Safing at https://github.com/safing/intel-data
# License: CC-BY-SA-4.0
# Domains used be the malicious new maintainer of the "The Great Suspender" Browser Extension.
# Ref: https://github.com/greatsuspender/thegreatsuspender/issues/1263
owebanalytics.com
trckpath.com
static.trckpath.com
trckingbyte.com
static.trckingbyte.com
# Malicious Cookie Stuffing Chrome Extensions
# 31.08.2022
# Ref: https://www.mcafee.com/blogs/other-blogs/mcafee-labs/malicious-cookie-stuffing-chrome-extensions-with-1-4-million-users/
netflixparty1.com
netflixpartyplus.com
flipshope.com
goscreenshotting.com
langhort.com
unscart.in
autobuyapp.com
WOW! 12 url:s!!!
And McAfee as source. WTF?!?!
If these are the lists portmaster is using, It’s a JOKE!!!
Compared to my hundreds of thousands of url:s in the maintained lists I’m using on the completely free software pihole. LMAO
You were saying?
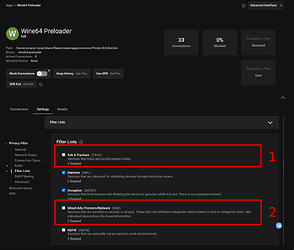
@Zesko if you see a link to anything containting any lists there, you either have a payed version or my install is broken, I see exactly what you took a screenshot of, but what that does (ie the lists of url:s) are nowhere to be found. And like above, did you check the content of the lists on the github?
Blocking ports, sure, its a great software for that.
Remove the blocking and make that paywalled as well then, only leave the port free, that would solve everything and I would even agree to it, but half-assing something and then luring ppl in and then when things that SHOULD be available in free version are behind a paywall, I see that as pretty trashy.
The advertise portmaster as free for blocking ports AND filter lists.
Pawyall for network hostory (not what im looking for), bandwith visibility, safing support and safing privacy network.
Subscription model, yeah, we all love that right?
Pormaster seems to leak traffic, that to me is the opposite of what a program like this should do.
What it does is remove the “protection” you have implemented on your network (bypassing pihole) AND stop blocking. Seems great!