Thanks @xabbu.
My Setup:
OpenWrt 21.02.1, r16325-88151b8303
Raspberry Pi 4 B+
root@OPENWRT:/etc/openvpn# openvpn --version
OpenVPN 2.5.3 aarch64-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD]
library versions: OpenSSL 1.1.1l 24 Aug 2021, LZO 2.10
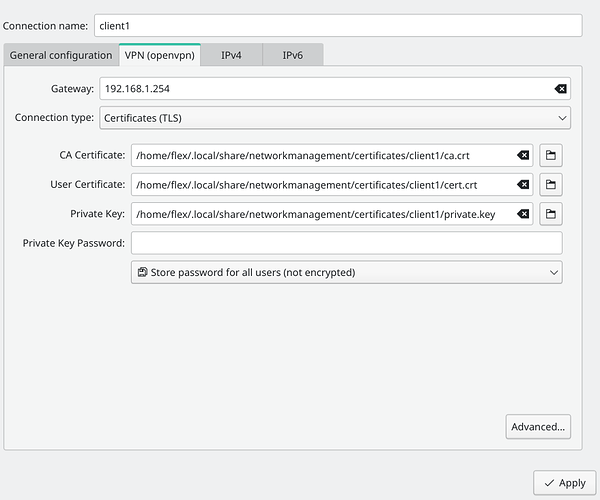
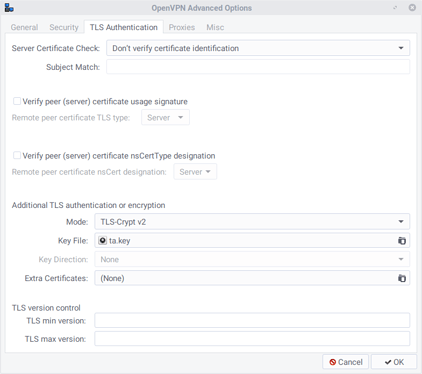
I installed OpenVPN on my OpenWrt router using a step by step guide from the OpenWrt website. The end result is a client.ovpn file and a server.conf. I enter the client.ovpn file in to Manjaro Network Manager but actually I don’t think I am doing it correctly. As you mentioned, there is an Advanced Button with a TLS Settings Tab and in there is a place to specify a “Mode” (tls-auth or tls-crypt) and a key file. But I don’t enter anything in there at all.
What am I supposed to put in there? Maybe what I have (tls-crypt-v2 stuff) won’t be compatible anyway? because I have a feeling that my NetworkManager does not support tls-crypt-v2.
[flex@inspiron7520 OpenWrt]$ pacman -Qi networkmanager-openvpn
Name : networkmanager-openvpn
Version : 1.8.16-1
Description : NetworkManager VPN plugin for OpenVPN
Architecture : x86_64
...
...
This is my client config file… client1.ovpn:
user nobody
group nogroup
dev tun
nobind
client
remote 192.168.1.254 1194 tcp
auth-nocache
remote-cert-tls server
<tls-crypt-v2>
-----BEGIN OpenVPN tls-crypt-v2 client key-----
-----END OpenVPN tls-crypt-v2 client key-----
</tls-crypt-v2>
<key>
-----BEGIN PRIVATE KEY-----
-----END PRIVATE KEY-----
</key>
<cert>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</cert>
<ca>
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
</ca>
When I enter your command from Konsole Terminal:
sudo openvpn client1.ovpn
This is what I get:
[flex@inspiron7520 OpenWrt]$ sudo openvpn client1.ovpn
[sudo] password for flex:
2022-01-05 20:27:23 us=303197 --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers.
2022-01-05 20:27:23 us=303397 Current Parameter Settings:
2022-01-05 20:27:23 us=303412 config = 'client1.ovpn'
2022-01-05 20:27:23 us=303421 mode = 0
2022-01-05 20:27:23 us=303429 persist_config = DISABLED
2022-01-05 20:27:23 us=303436 persist_mode = 1
2022-01-05 20:27:23 us=303443 show_ciphers = DISABLED
2022-01-05 20:27:23 us=303455 show_digests = DISABLED
2022-01-05 20:27:23 us=303470 show_engines = DISABLED
2022-01-05 20:27:23 us=303486 genkey = DISABLED
2022-01-05 20:27:23 us=303501 genkey_filename = '[UNDEF]'
2022-01-05 20:27:23 us=303515 key_pass_file = '[UNDEF]'
2022-01-05 20:27:23 us=303529 show_tls_ciphers = DISABLED
2022-01-05 20:27:23 us=303543 connect_retry_max = 0
2022-01-05 20:27:23 us=303556 Connection profiles [0]:
2022-01-05 20:27:23 us=303569 proto = tcp-client
2022-01-05 20:27:23 us=303582 local = '[UNDEF]'
2022-01-05 20:27:23 us=303594 local_port = '[UNDEF]'
2022-01-05 20:27:23 us=303607 remote = '192.168.1.254'
2022-01-05 20:27:23 us=303619 remote_port = '1194'
2022-01-05 20:27:23 us=303631 remote_float = DISABLED
2022-01-05 20:27:23 us=303644 bind_defined = DISABLED
2022-01-05 20:27:23 us=303656 bind_local = DISABLED
2022-01-05 20:27:23 us=303669 bind_ipv6_only = DISABLED
2022-01-05 20:27:23 us=303682 connect_retry_seconds = 5
2022-01-05 20:27:23 us=303694 connect_timeout = 120
2022-01-05 20:27:23 us=303706 socks_proxy_server = '[UNDEF]'
2022-01-05 20:27:23 us=303719 socks_proxy_port = '[UNDEF]'
2022-01-05 20:27:23 us=303732 tun_mtu = 1500
2022-01-05 20:27:23 us=303744 tun_mtu_defined = ENABLED
2022-01-05 20:27:23 us=303756 link_mtu = 1500
2022-01-05 20:27:23 us=303769 link_mtu_defined = DISABLED
2022-01-05 20:27:23 us=303781 tun_mtu_extra = 0
2022-01-05 20:27:23 us=303793 tun_mtu_extra_defined = DISABLED
2022-01-05 20:27:23 us=303806 mtu_discover_type = -1
2022-01-05 20:27:23 us=303818 fragment = 0
2022-01-05 20:27:23 us=303830 mssfix = 1450
2022-01-05 20:27:23 us=303843 explicit_exit_notification = 0
2022-01-05 20:27:23 us=303855 tls_auth_file = '[UNDEF]'
2022-01-05 20:27:23 us=303867 key_direction = not set
2022-01-05 20:27:23 us=303879 tls_crypt_file = '[UNDEF]'
2022-01-05 20:27:23 us=303892 tls_crypt_v2_file = '[INLINE]'
2022-01-05 20:27:23 us=303905 Connection profiles END
2022-01-05 20:27:23 us=303917 remote_random = DISABLED
2022-01-05 20:27:23 us=303929 ipchange = '[UNDEF]'
2022-01-05 20:27:23 us=303942 dev = 'tun'
2022-01-05 20:27:23 us=303954 dev_type = '[UNDEF]'
2022-01-05 20:27:23 us=303966 dev_node = '[UNDEF]'
2022-01-05 20:27:23 us=303978 lladdr = '[UNDEF]'
2022-01-05 20:27:23 us=303990 topology = 1
2022-01-05 20:27:23 us=304002 ifconfig_local = '[UNDEF]'
2022-01-05 20:27:23 us=304015 ifconfig_remote_netmask = '[UNDEF]'
2022-01-05 20:27:23 us=304027 ifconfig_noexec = DISABLED
2022-01-05 20:27:23 us=304039 ifconfig_nowarn = DISABLED
2022-01-05 20:27:23 us=304051 ifconfig_ipv6_local = '[UNDEF]'
2022-01-05 20:27:23 us=304064 ifconfig_ipv6_netbits = 0
2022-01-05 20:27:23 us=304076 ifconfig_ipv6_remote = '[UNDEF]'
2022-01-05 20:27:23 us=304088 shaper = 0
2022-01-05 20:27:23 us=304100 mtu_test = 0
2022-01-05 20:27:23 us=304112 mlock = DISABLED
2022-01-05 20:27:23 us=304125 keepalive_ping = 0
2022-01-05 20:27:23 us=304137 keepalive_timeout = 0
2022-01-05 20:27:23 us=304149 inactivity_timeout = 0
2022-01-05 20:27:23 us=304162 ping_send_timeout = 0
2022-01-05 20:27:23 us=304174 ping_rec_timeout = 0
2022-01-05 20:27:23 us=304186 ping_rec_timeout_action = 0
2022-01-05 20:27:23 us=304199 ping_timer_remote = DISABLED
2022-01-05 20:27:23 us=304211 remap_sigusr1 = 0
2022-01-05 20:27:23 us=304227 persist_tun = DISABLED
2022-01-05 20:27:23 us=304239 persist_local_ip = DISABLED
2022-01-05 20:27:23 us=304252 persist_remote_ip = DISABLED
2022-01-05 20:27:23 us=304264 persist_key = DISABLED
2022-01-05 20:27:23 us=304276 passtos = DISABLED
2022-01-05 20:27:23 us=304289 resolve_retry_seconds = 1000000000
2022-01-05 20:27:23 us=304301 resolve_in_advance = DISABLED
2022-01-05 20:27:23 us=304313 username = 'nobody'
2022-01-05 20:27:23 us=304325 groupname = 'nogroup'
2022-01-05 20:27:23 us=304337 chroot_dir = '[UNDEF]'
2022-01-05 20:27:23 us=304349 cd_dir = '[UNDEF]'
2022-01-05 20:27:23 us=304361 writepid = '[UNDEF]'
2022-01-05 20:27:23 us=304373 up_script = '[UNDEF]'
2022-01-05 20:27:23 us=304385 down_script = '[UNDEF]'
2022-01-05 20:27:23 us=304397 down_pre = DISABLED
2022-01-05 20:27:23 us=304410 up_restart = DISABLED
2022-01-05 20:27:23 us=304422 up_delay = DISABLED
2022-01-05 20:27:23 us=304434 daemon = DISABLED
2022-01-05 20:27:23 us=304446 inetd = 0
2022-01-05 20:27:23 us=304458 log = DISABLED
2022-01-05 20:27:23 us=304471 suppress_timestamps = DISABLED
2022-01-05 20:27:23 us=304483 machine_readable_output = DISABLED
2022-01-05 20:27:23 us=304495 nice = 0
2022-01-05 20:27:23 us=304507 verbosity = 7
2022-01-05 20:27:23 us=304519 mute = 0
2022-01-05 20:27:23 us=304531 gremlin = 0
2022-01-05 20:27:23 us=304543 status_file = '[UNDEF]'
2022-01-05 20:27:23 us=304556 status_file_version = 1
2022-01-05 20:27:23 us=304568 status_file_update_freq = 60
2022-01-05 20:27:23 us=304580 occ = ENABLED
2022-01-05 20:27:23 us=304592 rcvbuf = 0
2022-01-05 20:27:23 us=304605 sndbuf = 0
2022-01-05 20:27:23 us=304617 mark = 0
2022-01-05 20:27:23 us=304629 sockflags = 0
2022-01-05 20:27:23 us=304641 fast_io = DISABLED
2022-01-05 20:27:23 us=304654 comp.alg = 0
2022-01-05 20:27:23 us=304666 comp.flags = 0
2022-01-05 20:27:23 us=304678 route_script = '[UNDEF]'
2022-01-05 20:27:23 us=304691 route_default_gateway = '[UNDEF]'
2022-01-05 20:27:23 us=304703 route_default_metric = 0
2022-01-05 20:27:23 us=304716 route_noexec = DISABLED
2022-01-05 20:27:23 us=304729 route_delay = 0
2022-01-05 20:27:23 us=304740 route_delay_window = 30
2022-01-05 20:27:23 us=304754 route_delay_defined = DISABLED
2022-01-05 20:27:23 us=304768 route_nopull = DISABLED
2022-01-05 20:27:23 us=304781 route_gateway_via_dhcp = DISABLED
2022-01-05 20:27:23 us=304793 allow_pull_fqdn = DISABLED
2022-01-05 20:27:23 us=304817 management_addr = '[UNDEF]'
2022-01-05 20:27:23 us=304843 management_port = '[UNDEF]'
2022-01-05 20:27:23 us=304853 management_user_pass = '[UNDEF]'
2022-01-05 20:27:23 us=304863 management_log_history_cache = 250
2022-01-05 20:27:23 us=304874 management_echo_buffer_size = 100
2022-01-05 20:27:23 us=304884 management_write_peer_info_file = '[UNDEF]'
2022-01-05 20:27:23 us=304894 management_client_user = '[UNDEF]'
2022-01-05 20:27:23 us=304904 management_client_group = '[UNDEF]'
2022-01-05 20:27:23 us=304915 management_flags = 0
2022-01-05 20:27:23 us=304925 shared_secret_file = '[UNDEF]'
2022-01-05 20:27:23 us=304935 key_direction = not set
2022-01-05 20:27:23 us=304945 ciphername = 'BF-CBC'
2022-01-05 20:27:23 us=304955 ncp_enabled = ENABLED
2022-01-05 20:27:23 us=304966 ncp_ciphers = 'AES-256-GCM:AES-128-GCM'
2022-01-05 20:27:23 us=304976 authname = 'SHA1'
2022-01-05 20:27:23 us=304986 prng_hash = 'SHA1'
2022-01-05 20:27:23 us=305006 prng_nonce_secret_len = 16
2022-01-05 20:27:23 us=305018 keysize = 0
2022-01-05 20:27:23 us=305030 engine = DISABLED
2022-01-05 20:27:23 us=305042 replay = ENABLED
2022-01-05 20:27:23 us=305053 mute_replay_warnings = DISABLED
2022-01-05 20:27:23 us=305066 replay_window = 64
2022-01-05 20:27:23 us=305078 replay_time = 15
2022-01-05 20:27:23 us=305089 packet_id_file = '[UNDEF]'
2022-01-05 20:27:23 us=305101 test_crypto = DISABLED
2022-01-05 20:27:23 us=305113 tls_server = DISABLED
2022-01-05 20:27:23 us=305125 tls_client = ENABLED
2022-01-05 20:27:23 us=305137 ca_file = '[INLINE]'
2022-01-05 20:27:23 us=305148 ca_path = '[UNDEF]'
2022-01-05 20:27:23 us=305160 dh_file = '[UNDEF]'
2022-01-05 20:27:23 us=305172 cert_file = '[INLINE]'
2022-01-05 20:27:23 us=305184 extra_certs_file = '[UNDEF]'
2022-01-05 20:27:23 us=305196 priv_key_file = '[INLINE]'
2022-01-05 20:27:23 us=305208 pkcs12_file = '[UNDEF]'
2022-01-05 20:27:23 us=305219 cipher_list = '[UNDEF]'
2022-01-05 20:27:23 us=305231 cipher_list_tls13 = '[UNDEF]'
2022-01-05 20:27:23 us=305243 tls_cert_profile = '[UNDEF]'
2022-01-05 20:27:23 us=305255 tls_verify = '[UNDEF]'
2022-01-05 20:27:23 us=305267 tls_export_cert = '[UNDEF]'
2022-01-05 20:27:23 us=305278 verify_x509_type = 0
2022-01-05 20:27:23 us=305290 verify_x509_name = '[UNDEF]'
2022-01-05 20:27:23 us=305302 crl_file = '[UNDEF]'
2022-01-05 20:27:23 us=305313 ns_cert_type = 0
2022-01-05 20:27:23 us=305326 remote_cert_ku[i] = 65535
2022-01-05 20:27:23 us=305337 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305349 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305360 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305372 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305384 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305396 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305408 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305420 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305431 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305443 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305455 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305466 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305478 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305490 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305502 remote_cert_ku[i] = 0
2022-01-05 20:27:23 us=305514 remote_cert_eku = 'TLS Web Server Authentication'
2022-01-05 20:27:23 us=305526 ssl_flags = 0
2022-01-05 20:27:23 us=305538 tls_timeout = 2
2022-01-05 20:27:23 us=305549 renegotiate_bytes = -1
2022-01-05 20:27:23 us=305561 renegotiate_packets = 0
2022-01-05 20:27:23 us=305573 renegotiate_seconds = 3600
2022-01-05 20:27:23 us=305585 handshake_window = 60
2022-01-05 20:27:23 us=305597 transition_window = 3600
2022-01-05 20:27:23 us=305609 single_session = DISABLED
2022-01-05 20:27:23 us=305621 push_peer_info = DISABLED
2022-01-05 20:27:23 us=305632 tls_exit = DISABLED
2022-01-05 20:27:23 us=305644 tls_crypt_v2_metadata = '[UNDEF]'
2022-01-05 20:27:23 us=305657 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305668 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305680 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305692 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305704 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305716 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305727 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305739 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305751 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305763 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305775 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305786 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305798 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305811 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305822 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305834 pkcs11_protected_authentication = DISABLED
2022-01-05 20:27:23 us=305847 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305859 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305870 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305882 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305894 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305906 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305917 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305929 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305941 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305953 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305965 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305977 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=305989 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=306000 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=306012 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=306024 pkcs11_private_mode = 00000000
2022-01-05 20:27:23 us=306036 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306047 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306059 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306070 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306082 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306094 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306106 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306118 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306129 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306141 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306153 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306164 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306176 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306188 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306200 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306212 pkcs11_cert_private = DISABLED
2022-01-05 20:27:23 us=306223 pkcs11_pin_cache_period = -1
2022-01-05 20:27:23 us=306235 pkcs11_id = '[UNDEF]'
2022-01-05 20:27:23 us=306247 pkcs11_id_management = DISABLED
2022-01-05 20:27:23 us=306261 server_network = 0.0.0.0
2022-01-05 20:27:23 us=306274 server_netmask = 0.0.0.0
2022-01-05 20:27:23 us=306293 server_network_ipv6 = ::
2022-01-05 20:27:23 us=306304 server_netbits_ipv6 = 0
2022-01-05 20:27:23 us=306317 server_bridge_ip = 0.0.0.0
2022-01-05 20:27:23 us=306330 server_bridge_netmask = 0.0.0.0
2022-01-05 20:27:23 us=306342 server_bridge_pool_start = 0.0.0.0
2022-01-05 20:27:23 us=306355 server_bridge_pool_end = 0.0.0.0
2022-01-05 20:27:23 us=306366 ifconfig_pool_defined = DISABLED
2022-01-05 20:27:23 us=306380 ifconfig_pool_start = 0.0.0.0
2022-01-05 20:27:23 us=306392 ifconfig_pool_end = 0.0.0.0
2022-01-05 20:27:23 us=306405 ifconfig_pool_netmask = 0.0.0.0
2022-01-05 20:27:23 us=306416 ifconfig_pool_persist_filename = '[UNDEF]'
2022-01-05 20:27:23 us=306428 ifconfig_pool_persist_refresh_freq = 600
2022-01-05 20:27:23 us=306440 ifconfig_ipv6_pool_defined = DISABLED
2022-01-05 20:27:23 us=306452 ifconfig_ipv6_pool_base = ::
2022-01-05 20:27:23 us=306464 ifconfig_ipv6_pool_netbits = 0
2022-01-05 20:27:23 us=306476 n_bcast_buf = 256
2022-01-05 20:27:23 us=306488 tcp_queue_limit = 64
2022-01-05 20:27:23 us=306500 real_hash_size = 256
2022-01-05 20:27:23 us=306512 virtual_hash_size = 256
2022-01-05 20:27:23 us=306523 client_connect_script = '[UNDEF]'
2022-01-05 20:27:23 us=306535 learn_address_script = '[UNDEF]'
2022-01-05 20:27:23 us=306546 client_disconnect_script = '[UNDEF]'
2022-01-05 20:27:23 us=306558 client_config_dir = '[UNDEF]'
2022-01-05 20:27:23 us=306570 ccd_exclusive = DISABLED
2022-01-05 20:27:23 us=306582 tmp_dir = '/tmp'
2022-01-05 20:27:23 us=306593 push_ifconfig_defined = DISABLED
2022-01-05 20:27:23 us=306606 push_ifconfig_local = 0.0.0.0
2022-01-05 20:27:23 us=306619 push_ifconfig_remote_netmask = 0.0.0.0
2022-01-05 20:27:23 us=306631 push_ifconfig_ipv6_defined = DISABLED
2022-01-05 20:27:23 us=306644 push_ifconfig_ipv6_local = ::/0
2022-01-05 20:27:23 us=306656 push_ifconfig_ipv6_remote = ::
2022-01-05 20:27:23 us=306668 enable_c2c = DISABLED
2022-01-05 20:27:23 us=306680 duplicate_cn = DISABLED
2022-01-05 20:27:23 us=306691 cf_max = 0
2022-01-05 20:27:23 us=306703 cf_per = 0
2022-01-05 20:27:23 us=306715 max_clients = 1024
2022-01-05 20:27:23 us=306727 max_routes_per_client = 256
2022-01-05 20:27:23 us=306739 auth_user_pass_verify_script = '[UNDEF]'
2022-01-05 20:27:23 us=306751 auth_user_pass_verify_script_via_file = DISABLED
2022-01-05 20:27:23 us=306763 auth_token_generate = DISABLED
2022-01-05 20:27:23 us=306774 auth_token_lifetime = 0
2022-01-05 20:27:23 us=306786 auth_token_secret_file = '[UNDEF]'
2022-01-05 20:27:23 us=306797 port_share_host = '[UNDEF]'
2022-01-05 20:27:23 us=306809 port_share_port = '[UNDEF]'
2022-01-05 20:27:23 us=306821 vlan_tagging = DISABLED
2022-01-05 20:27:23 us=306833 vlan_accept = all
2022-01-05 20:27:23 us=306845 vlan_pvid = 1
2022-01-05 20:27:23 us=306857 client = ENABLED
2022-01-05 20:27:23 us=306869 pull = ENABLED
2022-01-05 20:27:23 us=306880 auth_user_pass_file = '[UNDEF]'
2022-01-05 20:27:23 us=306895 OpenVPN 2.5.4 [git:makepkg/3f7a85b9aebe7be0+] x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Oct 5 2021
2022-01-05 20:27:23 us=306916 library versions: OpenSSL 1.1.1l 24 Aug 2021, LZO 2.10
2022-01-05 20:27:23 us=306988 WARNING: you are using user/group/chroot/setcon without persist-tun -- this may cause restarts to fail
2022-01-05 20:27:23 us=307001 WARNING: you are using user/group/chroot/setcon without persist-key -- this may cause restarts to fail
2022-01-05 20:27:23 us=307675 PRNG init md=SHA1 size=36
2022-01-05 20:27:23 us=307718 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2022-01-05 20:27:23 us=307741 Outgoing Control Channel Encryption: CIPHER KEY: d43cbb57 10d7f430 526fa23f 77c07396 d5bb162e 4adec223 ac0cdc00 f35addeb
2022-01-05 20:27:23 us=307755 Outgoing Control Channel Encryption: CIPHER block_size=16 iv_size=16
2022-01-05 20:27:23 us=307780 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2022-01-05 20:27:23 us=307800 Outgoing Control Channel Encryption: HMAC KEY: e5b4c942 c9f91925 57564fa8 7391cd96 d82cdb98 565eca54 a6f36dc2 b3ad150d
2022-01-05 20:27:23 us=307811 Outgoing Control Channel Encryption: HMAC size=32 block_size=32
2022-01-05 20:27:23 us=307826 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2022-01-05 20:27:23 us=307844 Incoming Control Channel Encryption: CIPHER KEY: fb0eef5e d1662a0d 35f5f5d5 a5f3c0b8 34e3e47d 9a1d5c5c c5bf5373 9e471a1f
2022-01-05 20:27:23 us=307857 Incoming Control Channel Encryption: CIPHER block_size=16 iv_size=16
2022-01-05 20:27:23 us=307874 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2022-01-05 20:27:23 us=307892 Incoming Control Channel Encryption: HMAC KEY: c1c1d44f 3e1f7073 1db36d0c 5abb1e42 35e14f0f f7054c51 e8f1afe3 375e24d0
2022-01-05 20:27:23 us=307903 Incoming Control Channel Encryption: HMAC size=32 block_size=32
2022-01-05 20:27:23 us=307918 tls_crypt_adjust_frame_parameters: Adjusting frame parameters for tls-crypt by 56 bytes
2022-01-05 20:27:23 us=307938 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:27:23 us=307988 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:27:23 us=308010 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:27:23 us=308044 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:27:23 us=308060 Control Channel MTU parms [ L:1623 D:1154 EF:96 EB:0 ET:0 EL:3 ]
2022-01-05 20:27:23 us=308090 MTU DYNAMIC mtu=1450, flags=2, 1623 -> 1450
2022-01-05 20:27:23 us=308120 RESOLVE_REMOTE flags=0x0101 phase=1 rrs=0 sig=-1 status=0
2022-01-05 20:27:23 us=308145 Data Channel MTU parms [ L:1623 D:1450 EF:123 EB:406 ET:0 EL:3 ]
2022-01-05 20:27:23 us=308171 crypto_adjust_frame_parameters: Adjusting frame parameters for crypto by 40 bytes
2022-01-05 20:27:23 us=308184 calc_options_string_link_mtu: link-mtu 1623 -> 1543
2022-01-05 20:27:23 us=308207 crypto_adjust_frame_parameters: Adjusting frame parameters for crypto by 40 bytes
2022-01-05 20:27:23 us=308219 calc_options_string_link_mtu: link-mtu 1623 -> 1543
2022-01-05 20:27:23 us=308238 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1543,tun-mtu 1500,proto TCPv4_CLIENT,auth SHA1,keysize 128,key-method 2,tls-client'
2022-01-05 20:27:23 us=308249 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1543,tun-mtu 1500,proto TCPv4_SERVER,auth SHA1,keysize 128,key-method 2,tls-server'
2022-01-05 20:27:23 us=309885 failed to find GID for group nogroup
2022-01-05 20:27:23 us=309905 Exiting due to fatal error
[flex@inspiron7520 OpenWrt]$
Does that error mean I should create the group: “nogroup” in Manjaro?
When I comment out the first two lines:
#user nobody
#group nogroup
I get an endless output like this… which looks like there is communication between the “openvpn” command in Manjaro command line and the server… although there is no mention of tls-crypt-v2:
.........
.............
................
2022-01-05 20:14:45 us=796537 OpenVPN 2.5.4 [git:makepkg/3f7a85b9aebe7be0+] x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Oct 5 2021
2022-01-05 20:14:45 us=796556 library versions: OpenSSL 1.1.1l 24 Aug 2021, LZO 2.10
2022-01-05 20:14:45 us=797344 PRNG init md=SHA1 size=36
2022-01-05 20:14:45 us=797385 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2022-01-05 20:14:45 us=797409 Outgoing Control Channel Encryption: CIPHER KEY: d43cbb57 10d7f430 526fa23f 77c07396 d5bb162e 4adec223 ac0cdc00 f35addeb
2022-01-05 20:14:45 us=797424 Outgoing Control Channel Encryption: CIPHER block_size=16 iv_size=16
2022-01-05 20:14:45 us=797450 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2022-01-05 20:14:45 us=797472 Outgoing Control Channel Encryption: HMAC KEY: e5b4c942 c9f91925 57564fa8 7391cd96 d82cdb98 565eca54 a6f36dc2 b3ad150d
2022-01-05 20:14:45 us=797483 Outgoing Control Channel Encryption: HMAC size=32 block_size=32
2022-01-05 20:14:45 us=797496 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2022-01-05 20:14:45 us=797514 Incoming Control Channel Encryption: CIPHER KEY: fb0eef5e d1662a0d 35f5f5d5 a5f3c0b8 34e3e47d 9a1d5c5c c5bf5373 9e471a1f
2022-01-05 20:14:45 us=797528 Incoming Control Channel Encryption: CIPHER block_size=16 iv_size=16
2022-01-05 20:14:45 us=797543 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2022-01-05 20:14:45 us=797563 Incoming Control Channel Encryption: HMAC KEY: c1c1d44f 3e1f7073 1db36d0c 5abb1e42 35e14f0f f7054c51 e8f1afe3 375e24d0
2022-01-05 20:14:45 us=797573 Incoming Control Channel Encryption: HMAC size=32 block_size=32
2022-01-05 20:14:45 us=797585 tls_crypt_adjust_frame_parameters: Adjusting frame parameters for tls-crypt by 56 bytes
2022-01-05 20:14:45 us=797604 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:14:45 us=797661 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:14:45 us=797676 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:14:45 us=797714 PID packet_id_init seq_backtrack=64 time_backtrack=15
2022-01-05 20:14:45 us=797730 Control Channel MTU parms [ L:1623 D:1154 EF:96 EB:0 ET:0 EL:3 ]
2022-01-05 20:14:45 us=797756 MTU DYNAMIC mtu=1450, flags=2, 1623 -> 1450
2022-01-05 20:14:45 us=797784 RESOLVE_REMOTE flags=0x0101 phase=1 rrs=0 sig=-1 status=0
2022-01-05 20:14:45 us=797798 Data Channel MTU parms [ L:1623 D:1450 EF:123 EB:406 ET:0 EL:3 ]
2022-01-05 20:14:45 us=797818 crypto_adjust_frame_parameters: Adjusting frame parameters for crypto by 40 bytes
2022-01-05 20:14:45 us=797831 calc_options_string_link_mtu: link-mtu 1623 -> 1543
2022-01-05 20:14:45 us=797851 crypto_adjust_frame_parameters: Adjusting frame parameters for crypto by 40 bytes
2022-01-05 20:14:45 us=797863 calc_options_string_link_mtu: link-mtu 1623 -> 1543
2022-01-05 20:14:45 us=797878 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1543,tun-mtu 1500,proto TCPv4_CLIENT,auth SHA1,keysize 128,key-method 2,tls-client'
2022-01-05 20:14:45 us=797890 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1543,tun-mtu 1500,proto TCPv4_SERVER,auth SHA1,keysize 128,key-method 2,tls-server'
2022-01-05 20:14:45 us=797911 TCP/UDP: Preserving recently used remote address: [AF_INET]192.168.1.254:1194
2022-01-05 20:14:45 us=797946 Socket Buffers: R=[131072->131072] S=[16384->16384]
2022-01-05 20:14:45 us=797960 Attempting to establish TCP connection with [AF_INET]192.168.1.254:1194 [nonblock]
2022-01-05 20:14:45 us=804416 TCP connection established with [AF_INET]192.168.1.254:1194
2022-01-05 20:14:45 us=804460 TCP_CLIENT link local: (not bound)
2022-01-05 20:14:45 us=804468 TCP_CLIENT link remote: [AF_INET]192.168.1.254:1194
2022-01-05 20:14:45 us=804503 TCP_CLIENT WRITE [353] to [AF_INET]192.168.1.254:1194: P_CONTROL_HARD_RESET_CLIENT_V3 kid=0 [ ] pid=353 DATA len=339
2022-01-05 20:14:45 us=815010 TCP_CLIENT READ [66] from [AF_INET]192.168.1.254:1194: P_CONTROL_HARD_RESET_SERVER_V2 kid=0 [ ] pid=353 DATA len=52
2022-01-05 20:14:45 us=815046 TLS: Initial packet from [AF_INET]192.168.1.254:1194, sid=11c5121a 03a66349
2022-01-05 20:14:45 us=815071 PID_TEST [0] [TLS_WRAP-0] [] 0:0 1641413684:1 t=1641413685[0] r=[0,64,15,0,1] sl=[0,0,64,528]
2022-01-05 20:14:45 us=815107 TCP_CLIENT WRITE [62] to [AF_INET]192.168.1.254:1194: P_ACK_V1 kid=0 [ ]
2022-01-05 20:14:45 us=815224 TCP_CLIENT WRITE [331] to [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=865 DATA len=317
2022-01-05 20:14:45 us=844382 TCP_CLIENT READ [1236] from [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=609 DATA len=1222
2022-01-05 20:14:45 us=844470 PID_TEST [0] [TLS_WRAP-0] [0] 1641413684:1 1641413684:2 t=1641413685[0] r=[0,64,15,0,1] sl=[63,1,64,528]
2022-01-05 20:14:45 us=845022 TCP_CLIENT WRITE [62] to [AF_INET]192.168.1.254:1194: P_ACK_V1 kid=0 [ ]
2022-01-05 20:14:45 us=845437 TCP_CLIENT READ [1224] from [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=865 DATA len=1210
2022-01-05 20:14:45 us=845497 PID_TEST [0] [TLS_WRAP-0] [00] 1641413684:2 1641413684:3 t=1641413685[0] r=[0,64,15,0,1] sl=[62,2,64,528]
2022-01-05 20:14:45 us=845898 VERIFY OK: depth=1, CN=ovpnca
2022-01-05 20:14:45 us=846167 VERIFY KU OK
2022-01-05 20:14:45 us=846192 Validating certificate extended key usage
2022-01-05 20:14:45 us=846207 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2022-01-05 20:14:45 us=846224 VERIFY EKU OK
2022-01-05 20:14:45 us=846239 VERIFY OK: depth=0, CN=server
2022-01-05 20:14:45 us=846437 TCP_CLIENT READ [71] from [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=1121 DATA len=57
2022-01-05 20:14:45 us=846470 PID_TEST [0] [TLS_WRAP-0] [000] 1641413684:3 1641413684:4 t=1641413685[0] r=[0,64,15,0,1] sl=[61,3,64,528]
2022-01-05 20:14:45 us=849979 TCP_CLIENT WRITE [62] to [AF_INET]192.168.1.254:1194: P_ACK_V1 kid=0 [ ]
2022-01-05 20:14:45 us=850080 TCP_CLIENT WRITE [1124] to [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=1633 DATA len=1110
2022-01-05 20:14:45 us=850122 TCP_CLIENT WRITE [1112] to [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=1889 DATA len=1098
2022-01-05 20:14:45 us=850176 TCP_CLIENT WRITE [433] to [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=2145 DATA len=419
2022-01-05 20:14:45 us=871451 TCP_CLIENT READ [62] from [AF_INET]192.168.1.254:1194: P_ACK_V1 kid=0 [ ]
2022-01-05 20:14:45 us=871532 PID_TEST [0] [TLS_WRAP-0] [0000] 1641413684:4 1641413684:5 t=1641413685[0] r=[0,64,15,0,1] sl=[60,4,64,528]
2022-01-05 20:14:45 us=876685 TCP_CLIENT READ [224] from [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=1633 DATA len=210
2022-01-05 20:14:45 us=876788 PID_TEST [0] [TLS_WRAP-0] [00000] 1641413684:5 1641413684:6 t=1641413685[0] r=[0,64,15,0,1] sl=[59,5,64,528]
2022-01-05 20:14:45 us=877024 TCP_CLIENT WRITE [62] to [AF_INET]192.168.1.254:1194: P_ACK_V1 kid=0 [ ]
2022-01-05 20:14:45 us=888748 TCP_CLIENT READ [273] from [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=1889 DATA len=259
2022-01-05 20:14:45 us=888827 PID_TEST [0] [TLS_WRAP-0] [000000] 1641413684:6 1641413684:7 t=1641413685[0] r=[0,64,15,0,1] sl=[58,6,64,528]
2022-01-05 20:14:45 us=888915 TCP_CLIENT WRITE [62] to [AF_INET]192.168.1.254:1194: P_ACK_V1 kid=0 [ ]
2022-01-05 20:14:45 us=889004 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
2022-01-05 20:14:45 us=889044 [server] Peer Connection Initiated with [AF_INET]192.168.1.254:1194
2022-01-05 20:14:45 us=892201 TCP_CLIENT READ [314] from [AF_INET]192.168.1.254:1194: P_CONTROL_V1 kid=0 [ ] pid=2145 DATA len=300
2022-01-05 20:14:45 us=892288 PID_TEST [0] [TLS_WRAP-0] [0000000] 1641413684:7 1641413684:8 t=1641413685[0] r=[0,64,15,0,1] sl=[57,7,64,528]
2022-01-05 20:14:45 us=892374 PUSH: Received control message: 'PUSH_REPLY,dhcp-option DNS 192.168.8.1,dhcp-option DOMAIN lan,redirect-gateway def1,persist-tun,persist-key,route-gateway 192.168.8.1,topology subnet,ping 10,ping-restart 60,ifconfig 192.168.8.2 255.255.255.0,peer-id 0,cipher AES-256-GCM'
2022-01-05 20:14:45 us=892517 OPTIONS IMPORT: timers and/or timeouts modified
2022-01-05 20:14:45 us=892539 OPTIONS IMPORT: --persist options modified
2022-01-05 20:14:45 us=892552 OPTIONS IMPORT: --ifconfig/up options modified
2022-01-05 20:14:45 us=892565 OPTIONS IMPORT: route options modified
2022-01-05 20:14:45 us=892579 OPTIONS IMPORT: route-related options modified
2022-01-05 20:14:45 us=892594 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
2022-01-05 20:14:45 us=892609 OPTIONS IMPORT: peer-id set
2022-01-05 20:14:45 us=892624 OPTIONS IMPORT: adjusting link_mtu to 1626
2022-01-05 20:14:45 us=892638 OPTIONS IMPORT: data channel crypto options modified
2022-01-05 20:14:45 us=892654 Data Channel: using negotiated cipher 'AES-256-GCM'
2022-01-05 20:14:45 us=892677 crypto_adjust_frame_parameters: Adjusting frame parameters for crypto by 48 bytes
2022-01-05 20:14:45 us=892694 MTU DYNAMIC mtu=1450, flags=2, 1554 -> 1450
2022-01-05 20:14:45 us=892712 Data Channel MTU parms [ L:1554 D:1450 EF:54 EB:406 ET:0 EL:3 ]
2022-01-05 20:14:45 us=892743 Client pre_master: 6474a980 acaaddd4 2762068b 01dbc3e0 152466ef 0891818d 6d13ab7e 3395a761 d3d86b83 eba9ed2b 42b4902b 06b116f8
2022-01-05 20:14:45 us=892769 Client random1: af59cf19 d3582bbd c4af4868 ac9d75a6 0d4f1b7c d97801a1 ff6a0acc da17e0d0
2022-01-05 20:14:45 us=892793 Client random2: 89a6b094 19af4fc6 d06b0e11 cbaa128b 5cd57c76 8cff90b2 e5578eaa 6128619f
2022-01-05 20:14:45 us=892823 Server pre_master: 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000 00000000
2022-01-05 20:14:45 us=892849 Server random1: f0d257ff 8a9e103d 073d4717 9a7b37d5 dba3f760 2f147186 1fb2940c e51572d3
2022-01-05 20:14:45 us=892873 Server random2: 8e8bc028 182087df cdd28416 a82e6699 eb2e440c 26d89a40 d6447e6c 2259b98d
2022-01-05 20:14:45 us=892901 tls1_P_hash sec: 6474a980 acaaddd4 2762068b 01dbc3e0 152466ef 0891818d
2022-01-05 20:14:45 us=892943 tls1_P_hash seed: 4f70656e 56504e20 6d617374 65722073 65637265 74af59cf 19d3582b bdc4af48 68ac9d75 a60d4f1b 7cd97801 a1ff6a0a ccda17e0 d0f0d257 ff8a9e10 3d073d47
......
........
..........
Now my questions are:
- Does networkmanager-openvpn v1.8.16-1 support tls-crypt-v2?
- If YES then the problem must be the way I am entering my client1.ovpn config file into NM so it can connect to OpenVPN? How do I use my client1.ovpn file to specify a “Mode” and “Key File” in the TLS Settings tab?
- If NO then should I rebuild the key config files using regular tls-crypt which I think NetworkManager supports. If so how do I do that?
Thank you very much,
Flex