This is the consequence of the now failing connectivity check - a domain is pinged every so often and if unreachable, the assumption is that there is no working internet connection.
You’d have to white list this domain, too
(or disable the check).
server=/xfinity.com/75.75.75.75
server=/xfinity.com/2001:558:feed::1
server=/xfinity.com/75.75.76.76
server=/xfinity.com/2001:558:feed::2
server=/google.com/75.75.75.75
server=/google.com/2001:558:feed::1
I tried adding this to my whitelist but I still get the same ? on my icon. Is it possible xfinitywifi doesn’t allow masking dns?
No … its not your ISP.
Config, example:
In this case … if using the check … you whitelist the uri it checks
/etc/NetworkManager/conf.d/20-connectivity.conf
[connectivity]
uri=https://www.archlinux.org/check_network_status.txt
interval=3200
Or you can disable it entirely:
/etc/NetworkManager/conf.d/21-connectivity.conf
[connectivity]
enabled=false
Ah yes, the original is at
So you can whitelist the uri found there … or use the config files like above to augment the function.
The url for the connectivity check can be found in:
/usr/lib/NetworkManager/conf.d/20-connectivity.conf
To change it, do not change it there, but instead copy the file to:
/etc/NetworkManager/conf.d/20-connectivity.conf
and edit it there - else it will be overwritten during updates.
… I just looked in my Xfce4 VM - there was no
/etc/NetworkManager/conf.d/20-connectivity.conf - it was only in /usr/lib/…
I disabled it and i don’t get that icon questionmark any more but I still don’t get pings from anything I whitelist
server=/manjaro.org/8.8.8.8
server=/manjaro.org/2001:4860:4860::8888
server=/xfinity.com/8.8.8.8
server=/xfinity.com/2001:4860:4860::8888
Those IPs are incorrect at a glance.
8.8.8.8 is google
And certainly xfinity and manjaros domains should not share the same IP.
You need the real ones.
$ dig manjaro.org | grep IN | tail -1
manjaro.org. 86360 IN A 116.203.91.91
$ dig xfinity.com | grep IN | tail -1
xfinity.com. 300 IN A 96.99.240.130
So your entries (for IPv4) should be
server=/manjaro.org/116.203.91.91
server=/xfinity.com/96.99.240.130
PS.
I find it kinda funny that earlier there was “/etc/hosts cant do this” … now the proposed method is … do the same thing using dnsmasq
PPS.
And remember … the big browsers dont use system DNS by default. ![]()
EDIT
Oops. It was supposed to be pointing towards a DNS server. ![]()
I guess i just don’t understand networking enough. I was just trying to copy what megavolt posted in his whitelist. Regardless i tried typing in the ip for each website like you just postedbut it still doesn’t work. ![]() I thought what megavolt was trying todo was traffic all the dns to googles 8.8.8.8 dns and i would just put each domain i wanted access to linked to that dns.
I thought what megavolt was trying todo was traffic all the dns to googles 8.8.8.8 dns and i would just put each domain i wanted access to linked to that dns. ![]() I appreciate you guys for trying tho.
I appreciate you guys for trying tho.
I had assumed it was pointing to the domain IP, but …
Indeed, looking again, pointing towards a DNS server may have been the intention.
![]() +
+ ![]()
If I am understanding your requirements, you have one machine that you want to run as a standalone device that will only serve one website?
If this is the case, I recommend setting up that device using UNBOUND and NXFILTER.
unbound is a recursive DNS lookup service, it pings the TLD for the ip address of the server that the domain is hosted and then caches that information. This way, the first time the site is accessed, it may take 230ms to resolve, but the next time is 0ms because it already knows the ip address.
NXFilter, is a DNS filter, once installed you can use it’s gui to configure your sites.
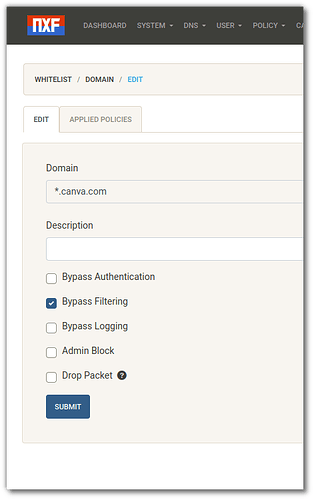
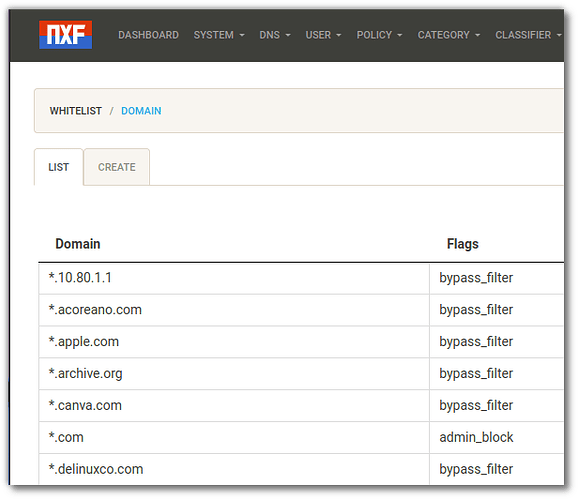
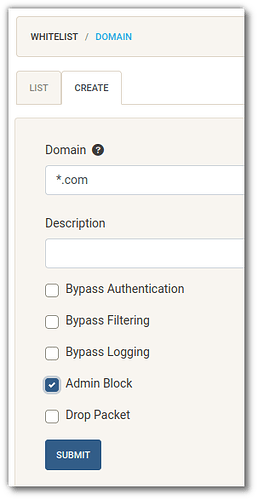
Once both apps are setup you can add items to the WHITELIST, to block all .com site, you would use a wildcard of *.com and set it to "Admin Block", but if you have a certain site that you still want to access, you add another WHITELIST entry but add it as a filter bypass. as an example, if I add canva.com, it would be the only .com site that the machine would be able to access.
Note: in order for NXFilter to work with Unbound, you will have to add a manual entry to NXFilter config, check out their forums for more info.
I have been using this setup for my residence and for my clients and it works well. I even used one system with Manjaro XFCE to setup a streaming server (an auction company that streams their sales), employees kept using it for personal use, now only the streaming host can be accessed, all other sites, they get a nastygram ![]()
Once setup, it is pretty much maintenance free and very flexible using the web GUI.
Hope this helps.
-John
Thanks John, unfortunately dns filtering requires direct control over dns settings. I use a public wifi network provided by comcast which i don’t have administative privileges. But that is a good solution for most homes
Internet provider is irrelevant, everything happens on the one machine.the rest of the network will not be affected.
Interesting, thanks for the suggestion I’ll check it out
ohh - I didn’t realise that - eyes read faster than brain can keep up and I had dnsmasq in my head because I looked at it as well ![]()
Did I mention… OpenSnitch?
I think I did, yes.
All suggestions here on DNS manipulation is too advanced for the usecase.
Using a customized application created for the task is the KISS principle in a nutshell.
It doesn’t fiddle with system network and address resolution but keeps a simple configuration of allowed sites.
Browsers has something called kiosk mode - but that is not doing what you want - as you can click any links on a page and navigate.
The concept you are looking for is not new and the use case is not new.
35 years ago I was member of a Visual Basic group and the founding member created a simple browser using the the inet.ocx and a configuration file. It was used a the school were he worked as janitor.
In AUR there is a build script for admbrowser (linked to github above) and it does exactly what you are looking for.
You can build and install it on the system, and if necessary remove whichever browser is installed.
Then configure the allowed websites in the configuration file.
pamac build admbrowser
I depends on
- python-pyqt5 (repo)
- python-yaml (repo)
- python-pyqt5-webengine (repo)
- qt5-webkit (aur)
It takes a short while to build - but you get exactly what you are looking for.
Simple, maintainable and thoroughly documented in the configuration /etc/admbrowser.yaml.
So can I assume, that you need to login through a website on that public network?
When you use my config, then just comment out the last 2 lines, like that:
# Block anything else
#address=/#/127.0.0.1
#address=/#/::1
That way it shouldn’t block anything. Instead I would suggest you to watch the log:
sudo tail -f /var/log/nm-dnsmasq.log
while trying to enter this website. Then you need to whitelist all Domains, which are requested. Usually a website also request different other Domains, which has to be in the whitelist as well.
It sound mostly pretty simple: Just put in the Domain, but actually nowadays websites rely on different other Domains.
Also, if you don’t care about the DNS-Server, then just add:
server=/xfinity.com/#
# is here a placeholder for “any” available DNS IP.